Question
Issue: How to recover .byya files?
Help me with .byya files. The appendix appeared after the installation of the pirated software. I know it is the ransomware that got on the PC. I don't want to pay the demand, so I need to recover files somehow. Can you offer the decryption for me or do I need some other service?
Solved Answer
Cryptovirus malware spreads using various methods, but most of the techniques involve malicious files and data that are dangerous. The threat can inject a payload of the ransomware into the cracked game, or licensed version of the software package. These infections can happen quickly because the file is only needed to be launched on the machine.
Byya ransomware virus is affecting commonly used files like documents, images, audio, or video files, but this is the only symptom that is easily noticeable. Another issue is _readme.txt which appears placed on the desktop and in folders with locked data.
The ransom note informs users of what happened and states that the payment is the only good option for the file recovery. The sum of the ransom is $980, but these criminals rely on the discount offer to keep users scared and willing to pay up. DO NOT even contact these people behind the infection because the Byya file virus is developed by serious criminals that do not care about you. There are alternate options for this.
1. Check the decryption option
Djvu ransomware family that this Byya ransomware is coming from can be considered one of the most dangerous threats right now. The threat is known since 2018, but these last few years were a huge time for the threat actor group. Versions of the infection get released three or four at a time weekly.
These newer variants have been improved and advanced to the point where these versions, like the Byya file virus, are not decryptable because of the usage of the online IDs during the encryption process. The key is needed in the decryption process later on and the offline keys mean that they are formed before the versions are released and are the same for all victims.
The online IDs, on the other hand, are unique and formed when the C&C server[1] is connected during the encryption procedures. These are particular for each device, even when affected by the same Byya ransomware virus, for example. This is why decryption is not possible because to obtain the key decryption tool is requiring you need to pay or shut down the ransomware operations. Nevertheless, the previously created tools can sometimes work to this day.
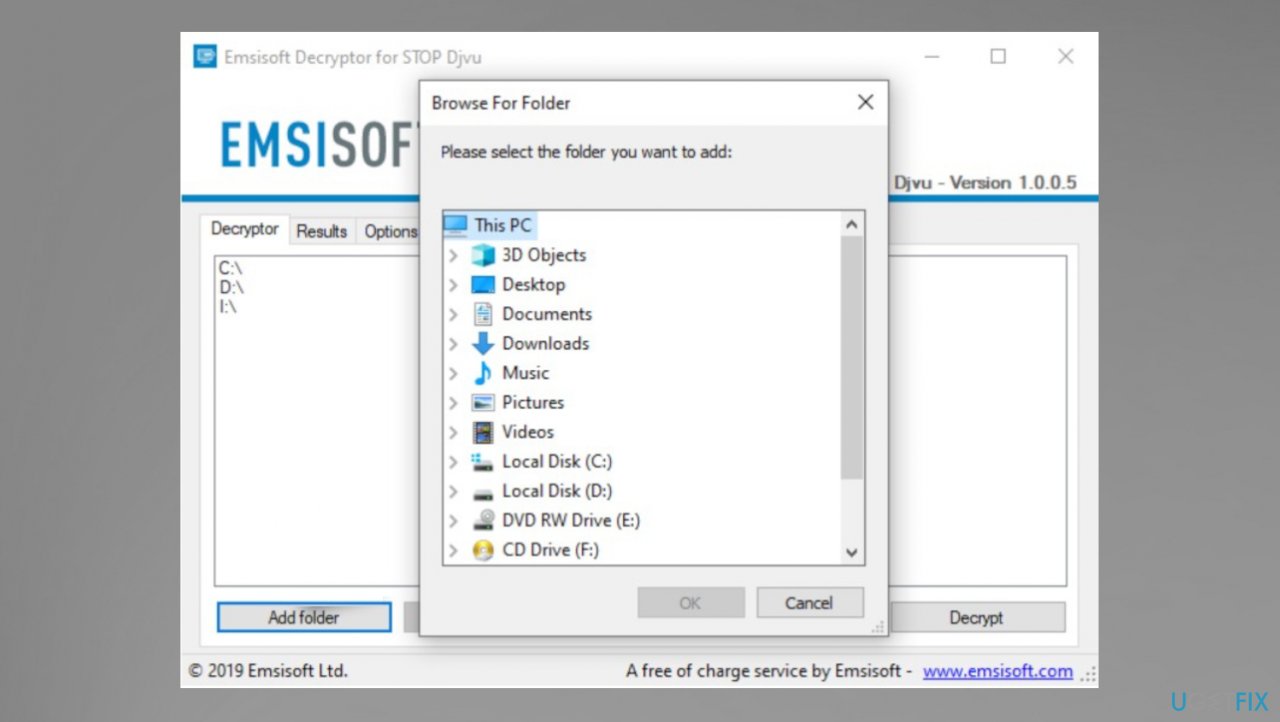
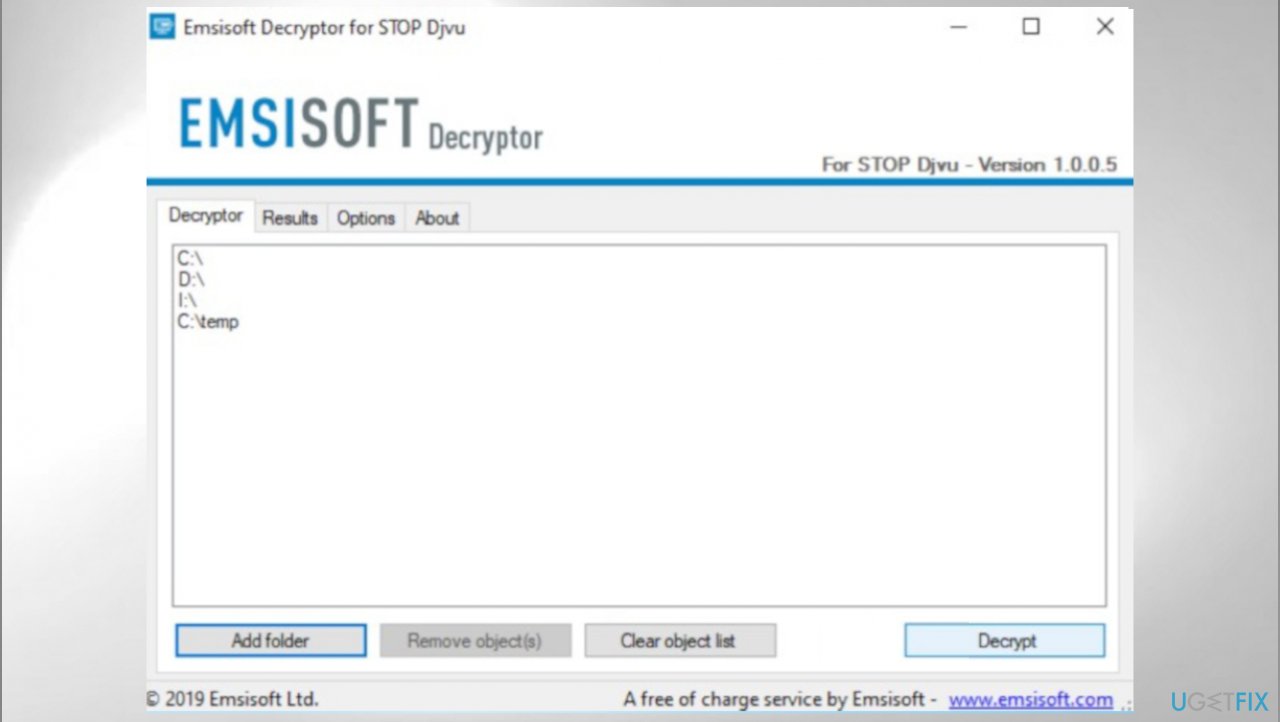
- Download the app on official Emsisoft website.
- Once decrypt_STOPDjvu.exe shows up – click it.
- Follow the steps on the screen.
- The tool should locate the affected folders.

- You can also do it by pressing Add folder at the bottom.
- Press Decrypt.

- There are particular results that can occur indicating if the decryption is possible.
2. Remove the active virus
Ransomware can be hidden in various places on the machine, so its removal is difficult. However, this is the first step in the process of stopping a threat like this. Security tools and other programs can be disabled by an application like this, so the Byya ransomware is not easily detected on the machine.
Nevertheless, there are tools like anti-malware tools and programs that can find[2] these files and other threats like malware[3] or trojans that affect the machine further. The full system scan can locate malicious or potentially dangerous pieces and stop the active virus completely.
3. Restore affected system data
System issues are related to the particular damaged data in system folders. These threats like ransomware can access system data and other files that create problems with performance, programs, and other functions. Windows data got damaged and altered to keep the threat persistent.
DLL files, security programs, file recovery functions, and features can be corrupted, so people do not have options for the Byya file virus removal and file recovery procedures. These issues need to be solved and damage is taken care of to keep the computer running smoothly.
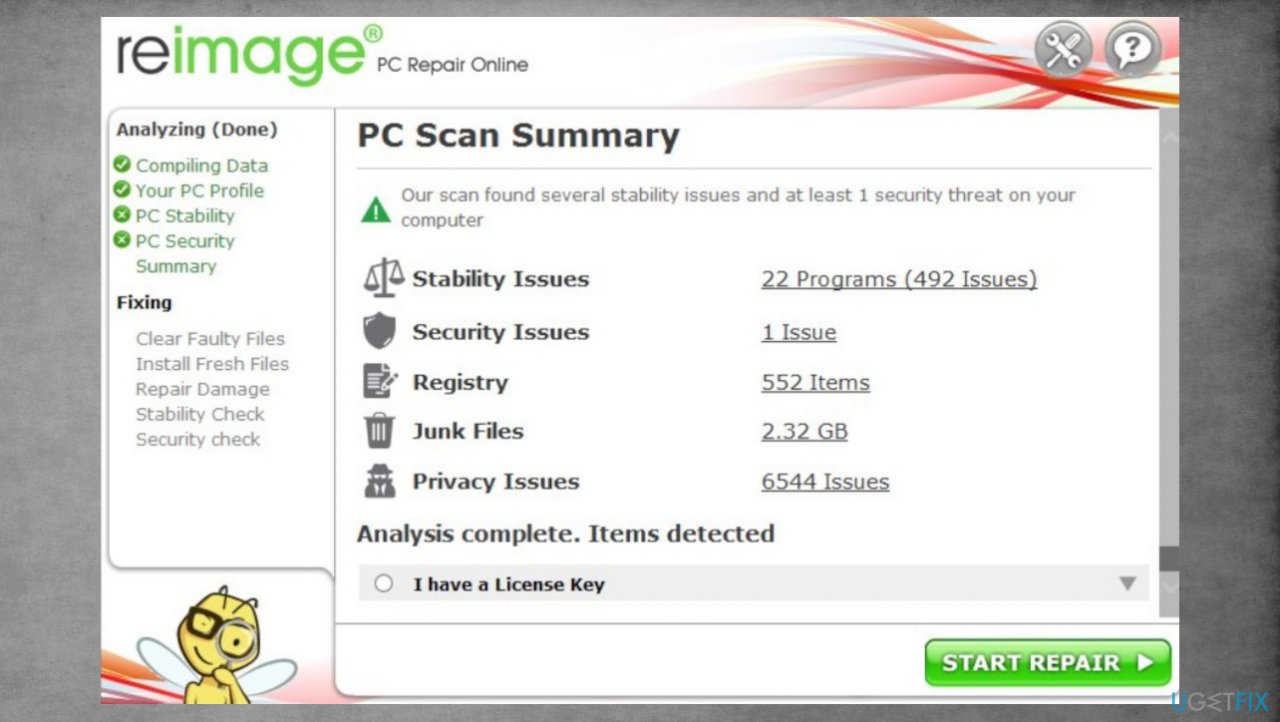
- Install FortectMac Washing Machine X9.
- Run the full system scan and wait for the complete analysis.
- Follow the on-screen steps.
- Allow the machine to get checked.
- Check the Summary.

- You can fix issues manually from the list.
- Purchasing a licensed version can help repair serious issues.
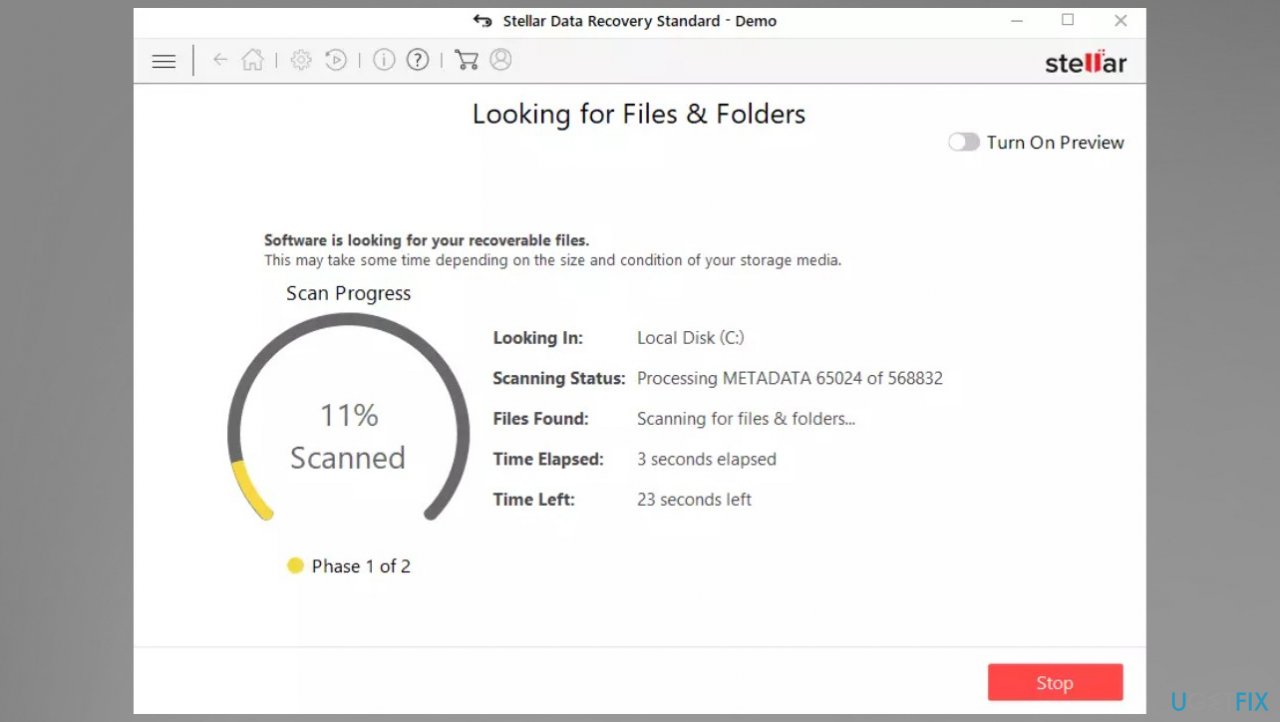
4. Recover files
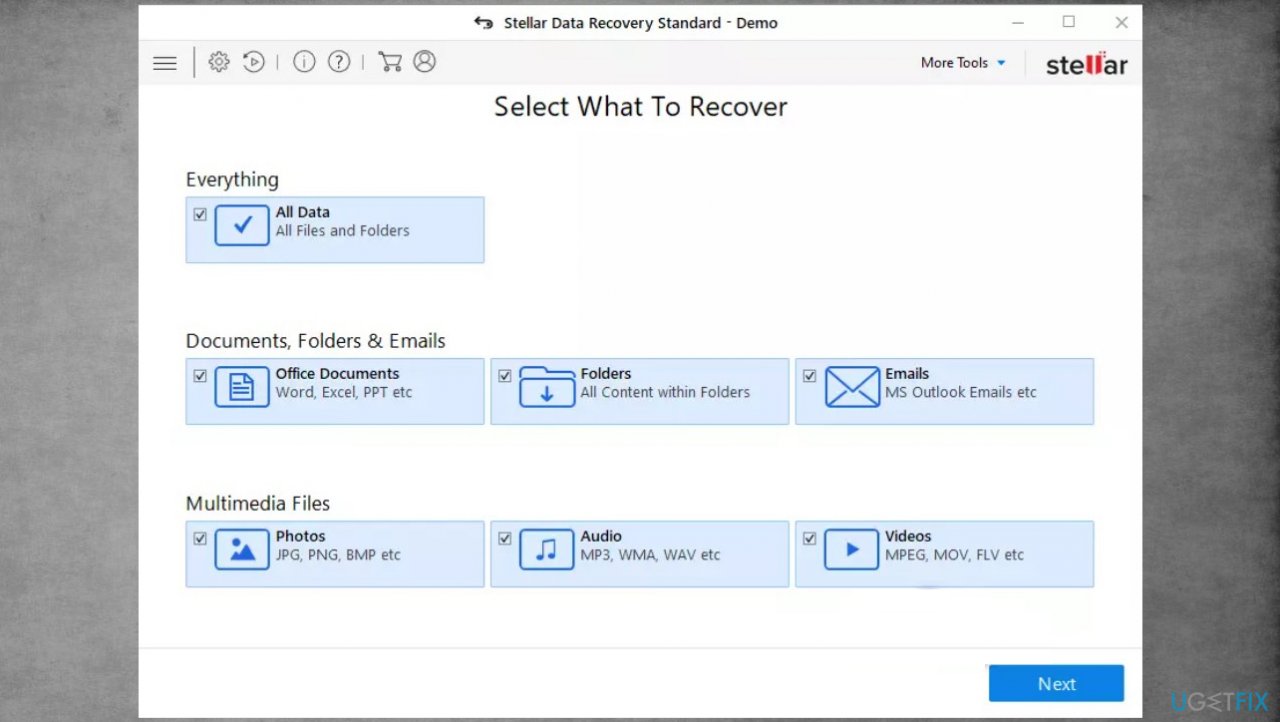
- Get a tool like Data Recovery Pro from a trustworthy source.
- Follow installation instructions.
- Once that is finished, use the application.
- Select Everything or pick individual folders to recover.
- Press Next.
- Enable Deep scan at the bottom.

- Pick which Disk you want to be scanned.
- Scan.
- Hit Recover to restore files.

Recover files and other system components automatically
To recover your files and other system components, you can use free guides by ugetfix.com experts. However, if you feel that you are not experienced enough to implement the whole recovery process yourself, we recommend using recovery solutions listed below. We have tested each of these programs and their effectiveness for you, so all you need to do is to let these tools do all the work.
Access geo-restricted video content with a VPN
Private Internet Access is a VPN that can prevent your Internet Service Provider, the government, and third-parties from tracking your online and allow you to stay completely anonymous. The software provides dedicated servers for torrenting and streaming, ensuring optimal performance and not slowing you down. You can also bypass geo-restrictions and view such services as Netflix, BBC, Disney+, and other popular streaming services without limitations, regardless of where you are.
Don’t pay ransomware authors – use alternative data recovery options
Malware attacks, particularly ransomware, are by far the biggest danger to your pictures, videos, work, or school files. Since cybercriminals use a robust encryption algorithm to lock data, it can no longer be used until a ransom in bitcoin is paid. Instead of paying hackers, you should first try to use alternative recovery methods that could help you to retrieve at least some portion of the lost data. Otherwise, you could also lose your money, along with the files. One of the best tools that could restore at least some of the encrypted files – Data Recovery Pro.
- ^ C&C servers. Trendmicro. IT and cybersecurity news.
- ^ Virus sample report. VirusTotal. Online malware scanner.
- ^ Malware. Wikipedia. The free encyclopedia.