Question
Issue: How to recover files after Jhgn ransomware attack?
Hey. I heed serious help. Files now are locked and useless on the computer. Jhgn virus locked them and demands money now. I don't believe the claim that decryption is possible here. Can you recover the files for me or is there anything I might do myself to solve this?
Solved Answer
Ransomware is a threat demanding payment in exchange for the alleged file decryption.[1] The sum is $980, and criminals even offer a 50% discount in the first 72 hours after the attack. These criminals behind the threat are not worthy of your trust, so paying the ransom is never recommended.
The best way to fight the threat is to remove it as soon as possible and right after those files get locked. The .jhgn appendix indicates the name of the threat and shows which data is damaged and made unopenable. Locked files are not permanently damaged unless the encryption happens again. However, there are no easy ways to solve the locked file issue when it comes to cryptovirus like this.
The file locking process is the encryption[2] using powerful algorithms that alter the original code of the file to make the piece useless. It is not permanent, but the damage might not be reversed without proper decryption tools. There is a need to recover these files or replace them with copies from a backup.

There are some options, however. These involve interference with the machine and additional tools. This Jhgn ransomware is coming from Djvu ransomware family, and the threat actors ensure that the virus is persistent and runs longer than it is needed, so users cannot repair files easily or at all.
1. Terminating the ransomware
Threat elimination requires anti-malware tools because the full system scan using a proper AV tool or the security program based on virus detection[3] can fully clear the machine from any cyber threats. Do not fall for the false claims that the people behind the virus list on the ransom note. There are no guarantees that criminals can or would restore those encrypted files for you.
The infection can be a result of the primary trojan or malware infiltration because ransomware is often a secondary payload in cyber attacks when attackers use exploits. These anti-malware tools can detect various malicious pieces and stop the active virus from moving further and damaging the machine more. Then you can deal with the encoded .jhgn files yourself.
2. Repairing affected system files
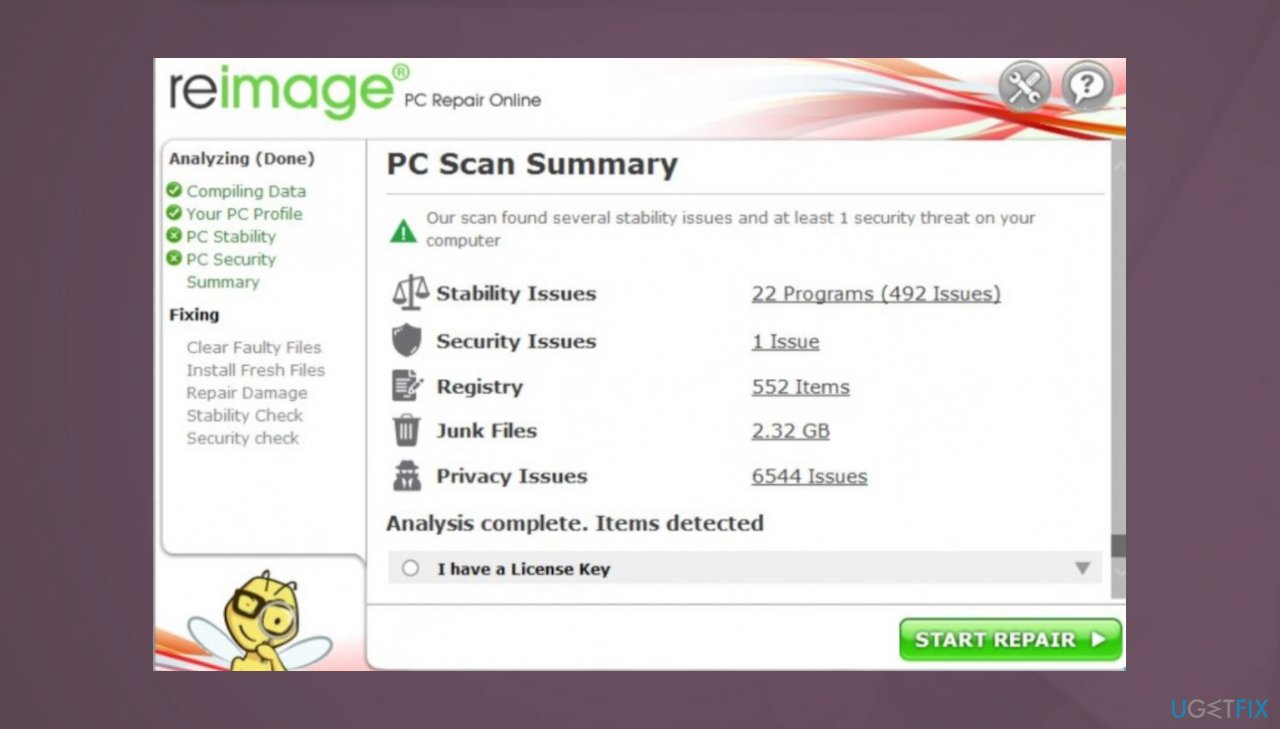
- Install FortectMac Washing Machine X9.
- Run the full system scan and wait for the analysis.
- Follow the on-screen instructions.
- Allow the machine to get checked.
- Check the Summary.

- You can fix issues manually from the list.
- Purchasing a licensed version can help repair serious issues.
3. Decrypting encrypted common data
Sometimes the file decryption is possible with these newer versions too because the connection and processes fail, so these offline ids get used instead of the online keys, and malware encodes files leaving the option for the recovery still. Try to run the tool and see if the recovery is possible in this instance.
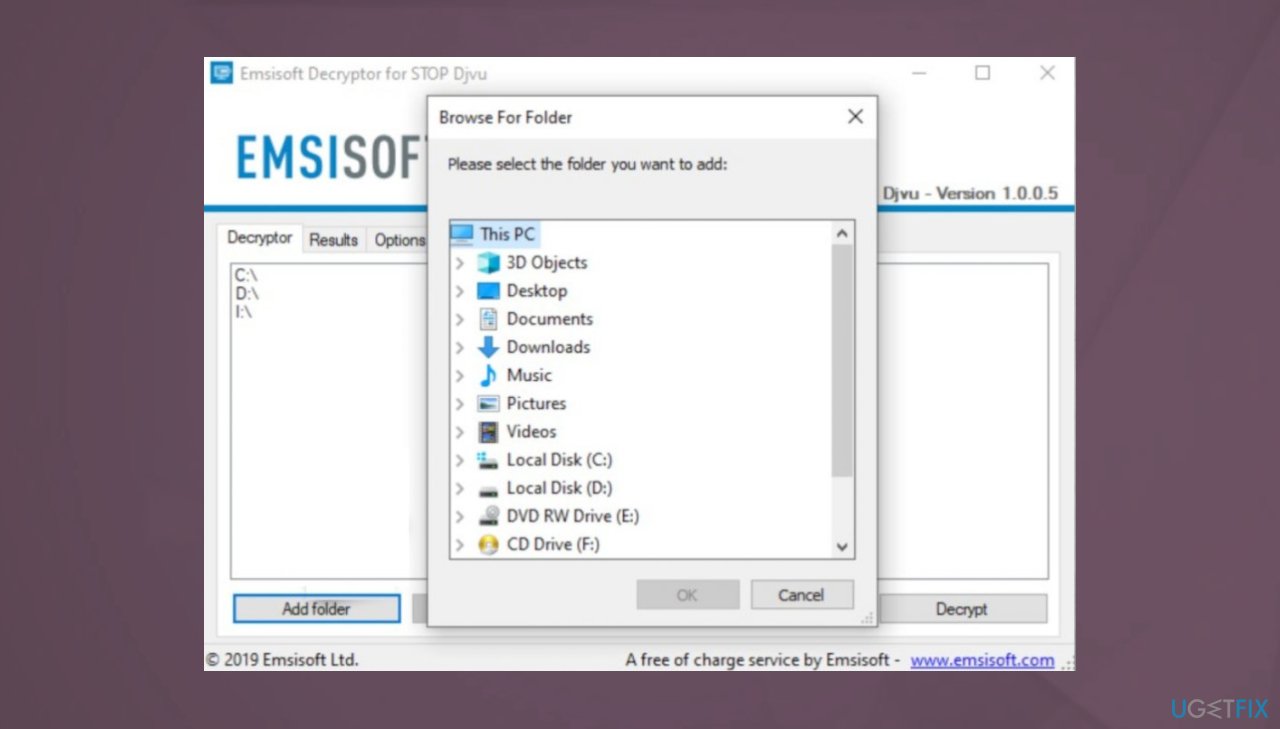
- Download the app on official Emsisoft website.
- Once decrypt_STOPDjvu.exe shows up – click it.
- Follow the steps on the screen.
- The tool should locate the affected folders.

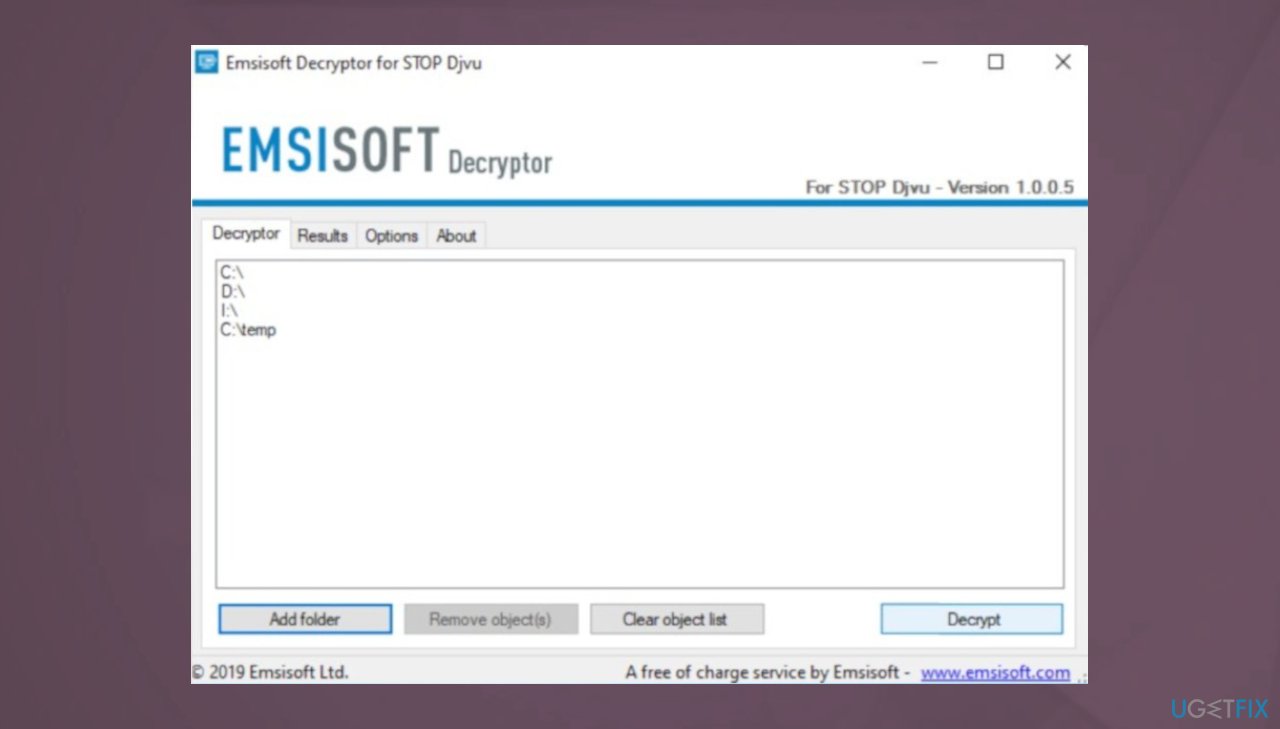
- You can also do it by pressing Add folder at the bottom.
- Press Decrypt.

- Results determine decryption options.
4. Restoring the data
- Get a tool for file repair. We can recommend Data Recovery Pro.
- Download from a trustworthy source.
- Follow installations until it is complete.
- Once that is finished, run the application.
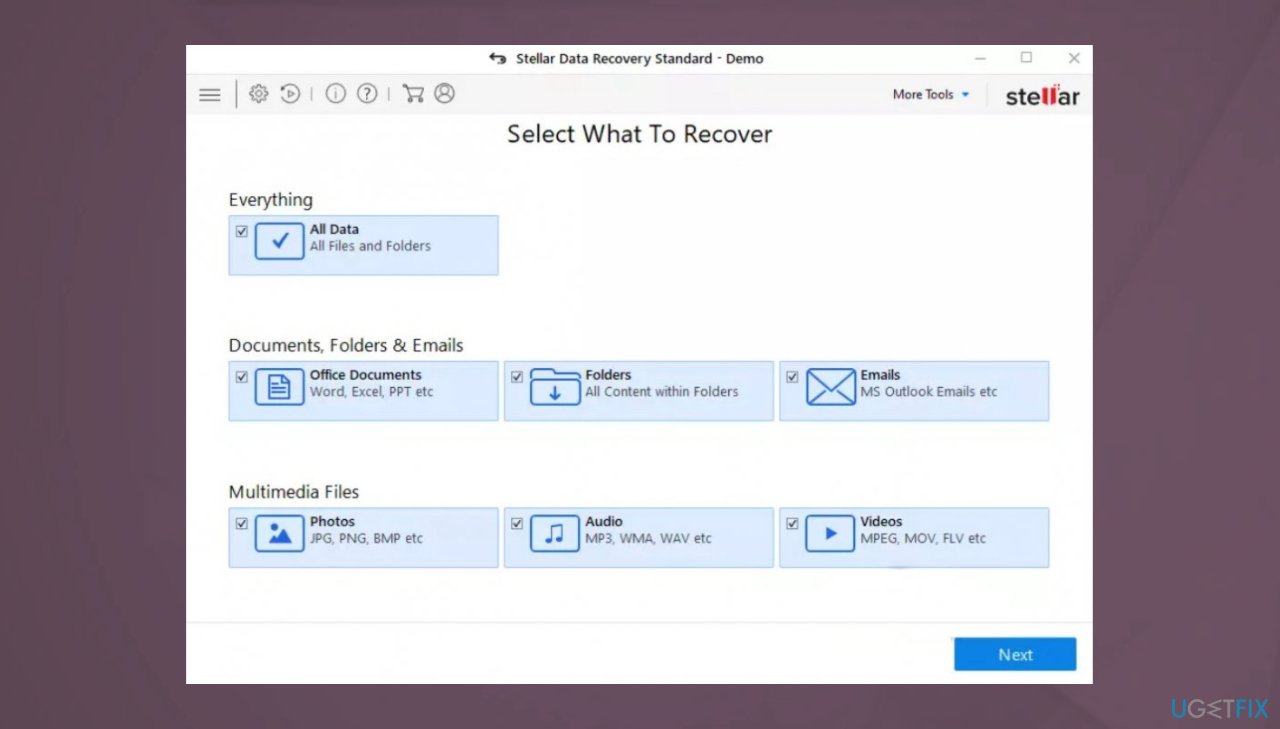
- Select Everything or pick individual folders/ files to recover.
- Press Next.

- Enable Deep scan at the bottom.
- Pick which Disk you want to be scanned.
- Scan.

- Hit Recover to restore files.
Recover files and other system components automatically
To recover your files and other system components, you can use free guides by ugetfix.com experts. However, if you feel that you are not experienced enough to implement the whole recovery process yourself, we recommend using recovery solutions listed below. We have tested each of these programs and their effectiveness for you, so all you need to do is to let these tools do all the work.
Prevent websites, ISP, and other parties from tracking you
To stay completely anonymous and prevent the ISP and the government from spying on you, you should employ Private Internet Access VPN. It will allow you to connect to the internet while being completely anonymous by encrypting all information, prevent trackers, ads, as well as malicious content. Most importantly, you will stop the illegal surveillance activities that NSA and other governmental institutions are performing behind your back.
Recover your lost files quickly
Unforeseen circumstances can happen at any time while using the computer: it can turn off due to a power cut, a Blue Screen of Death (BSoD) can occur, or random Windows updates can the machine when you went away for a few minutes. As a result, your schoolwork, important documents, and other data might be lost. To recover lost files, you can use Data Recovery Pro – it searches through copies of files that are still available on your hard drive and retrieves them quickly.
- ^ Becky Bracken. ‘Double-Extortion’ Ransomware Damage Skyrockets 935%. Threatpost. Malware news reports.
- ^ Encryption. Wikipedia. The free encyclopedia.
- ^ Virus detection rate. VirusTotal. Online malware scanner.