Question
Issue: How to restore files after Mpag ransomware attack?
Hello. I need your help. My files got locked with .mpag ransomware marker, and I need the option for recovery. I have no backups at all, so I am prepared to lose them all, but maybe there are some options there? Is it decryptable?
Solved Answer
The most important thing and the worst issue with these ransomware-type threats is the file-locking that cripples the system and frustrates users because their files get possibly permanently locked.[1] The infection can happen quickly without any symptoms on the machine, but once the data is locked and altered – ransomware is pretty much done with its operation.
From there, there are limited options for the system renewal and file recovery because ransomware creators ask for a large sum of money in Bitcoin for the possible file restoration, and the system requires serious repairs because processes can be significantly affected by any malware infections. Especially cryptovirus.[2]
What is this ransomware?
Mpag file virus is focusing on file locking because this is the option that can provide a reason behind the money demands. The threat can spread around using various tactics, but users[3] report the Djvu ransomware family versions reading mainly via torrents and pirating platforms because NBA video game cracks, software license versions, and other popular program packages can be sent with the malware payload.
The infection family is spreading since 2018, and it is more advanced since August 2019 when creators introduced the online id forming method to the mix and improved the encoding procedures. The infection is no longer decryptable since then. However, there are other options for file recovery.
Threat infiltrates the machine and relies on disturbing the processes further. Once the encoding is done the _readme.txt file is dropped on the machine and in various folders where these marked files can be found. Paying is not an option, so ignore these messages and do not contact the people behind the threat.
What can be done from here?
There are no tools that could 100% restore locked data or repair any other issues with the machine, but termination of the ransomware is possible and successful when the right tools are used. You need to remove the ransomware before doing anything about the Mpag ransomware file decryption because there is a high risk of getting files locked again if the virus is running.
We understand that your main focus and worry are those encoded files, but focus on virus removal, then repair system functions since there are a lot of features that can help with removal and recovery. Then, and only when the machine is virus-free can you rely on the file repair options. Those might include your backups, and these instances show how important it is to have those up to date.[4] Follow our tips thoroughly.
1. Terminate the infection
If you've been targeted by Mpag ransomware, don't pay the ransom! It is never an option. Anti-malware tools can remove any infection before unrecoverable damage occurs. Eliminating the threat is not the same as decryption. However, recovering files without eliminating an infestation will lead to permanent hardware damage on your computer or additional issues.
You should get a tool like anti-malware tools or a program running based on AV detection. This is the best way to find all malicious files and programs that can affect the computer. A full system scan indicates all those malicious pieces and helps you terminate the ransomware before recovering the affected data.
2. Repair corrupted data
Malware can do a lot of damage to your computer system besides the direct damage to those encoded files. Once it's installed, the virus will alter important sections like Windows' registry database and boot process to keep the threat running. You need to recover this corrupted data to have the machine running smoothly.
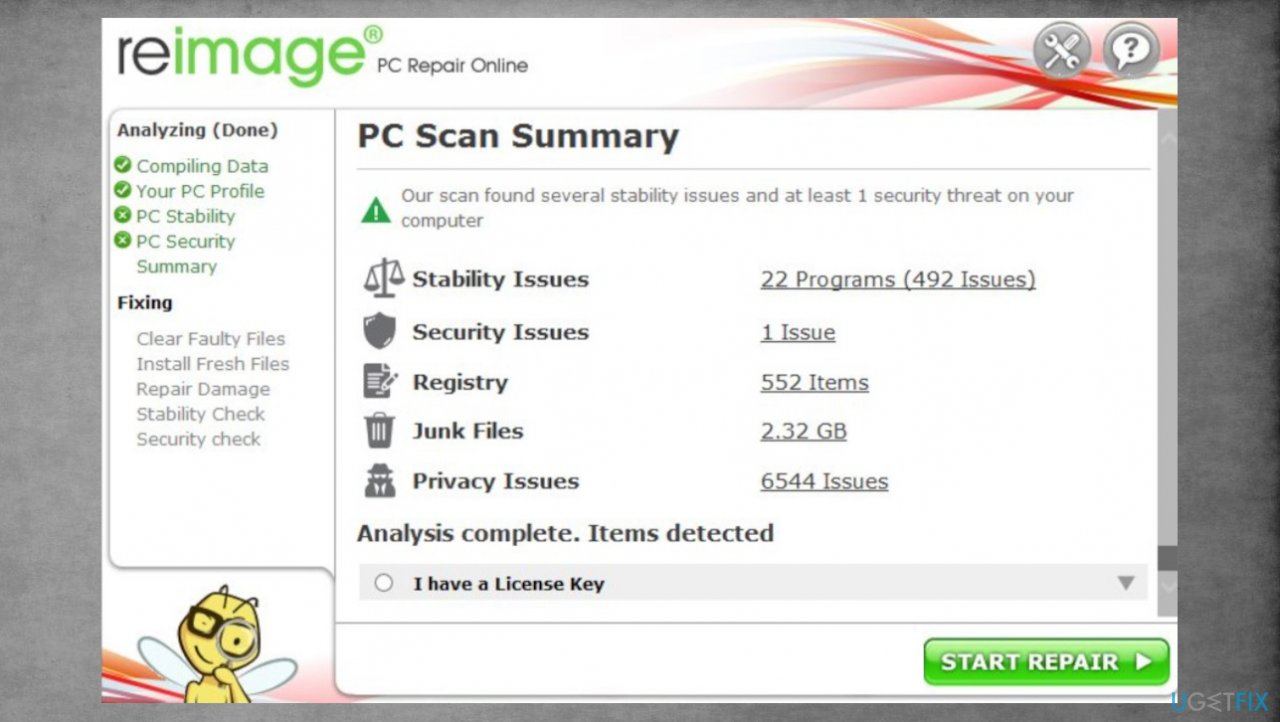
- Install FortectMac Washing Machine X9.
- Run the full system scan and wait for the complete analysis.
- Follow the on-screen steps.
- Allow the machine to get checked.
- Check the Summary.

- You can fix issues manually from the list.
- Purchasing a licensed version can help repair serious issues.
3. Check the possible decryption option
The malware research team was able to obtain decryption keys for the threats previously associated with this group, but now some new alterations to the virus mean people will never get their files back unless someone pays up. The decryption key is needed for each affected device because keys are created separately. The inline key method means that unique ids are made for each device that is affected by the same threat. Offline ids that are uniform with a version can be used for many machines. So you can try this tool still.
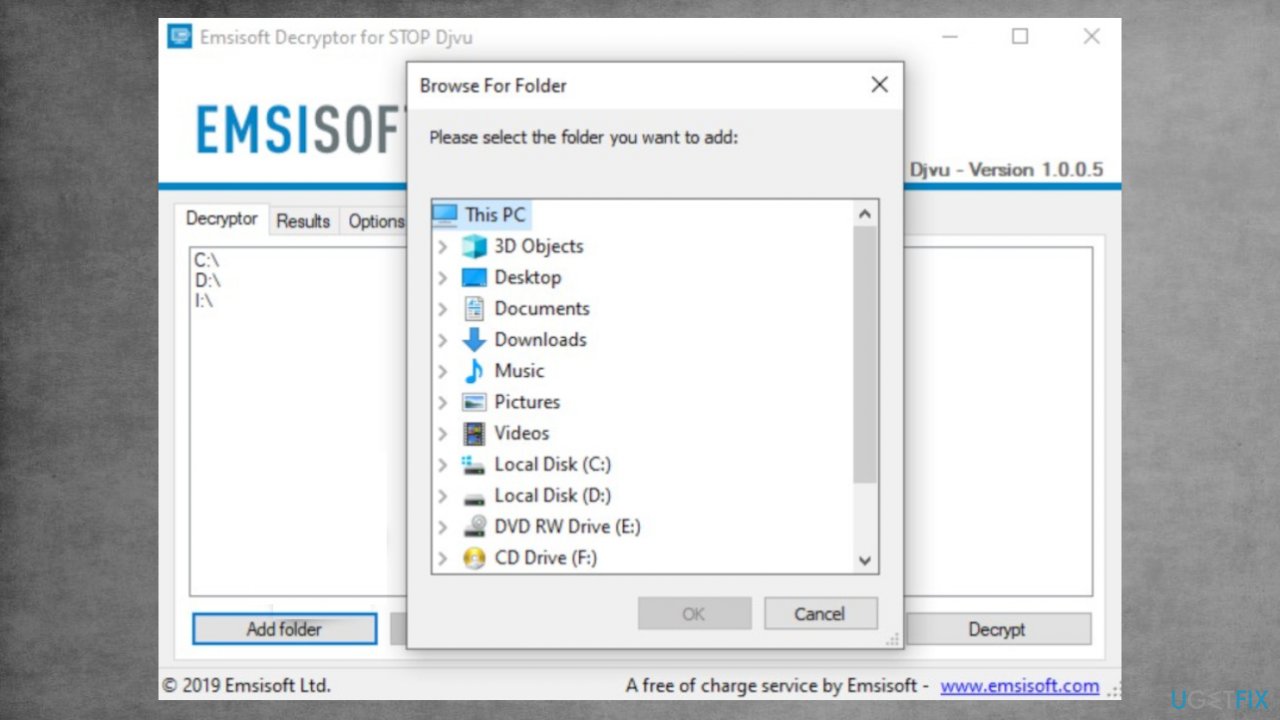
- Download the app on official Emsisoft website.
- Once decrypt_STOPDjvu.exe shows up – click it.
- Follow the steps on the screen.
- The tool should locate the affected folders.

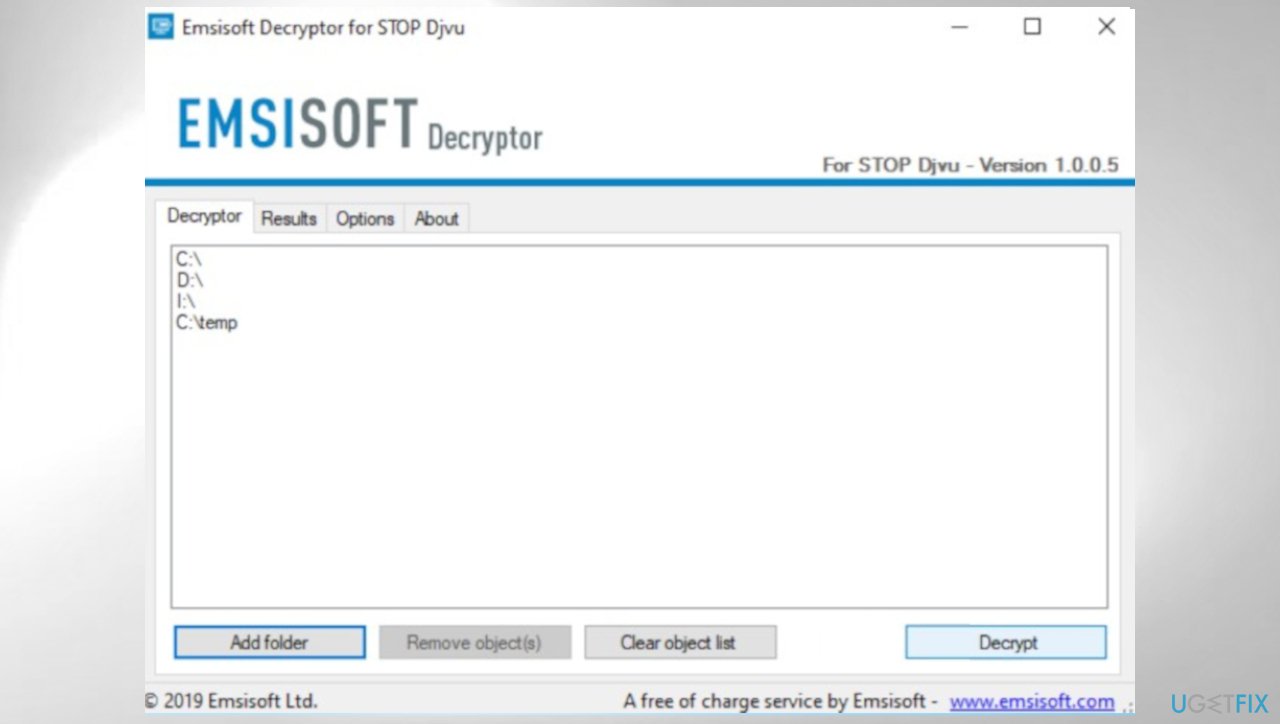
- You can also do it by pressing Add folder at the bottom.
- Press Decrypt.

- There are particular results that can occur indicating if the decryption is possible.
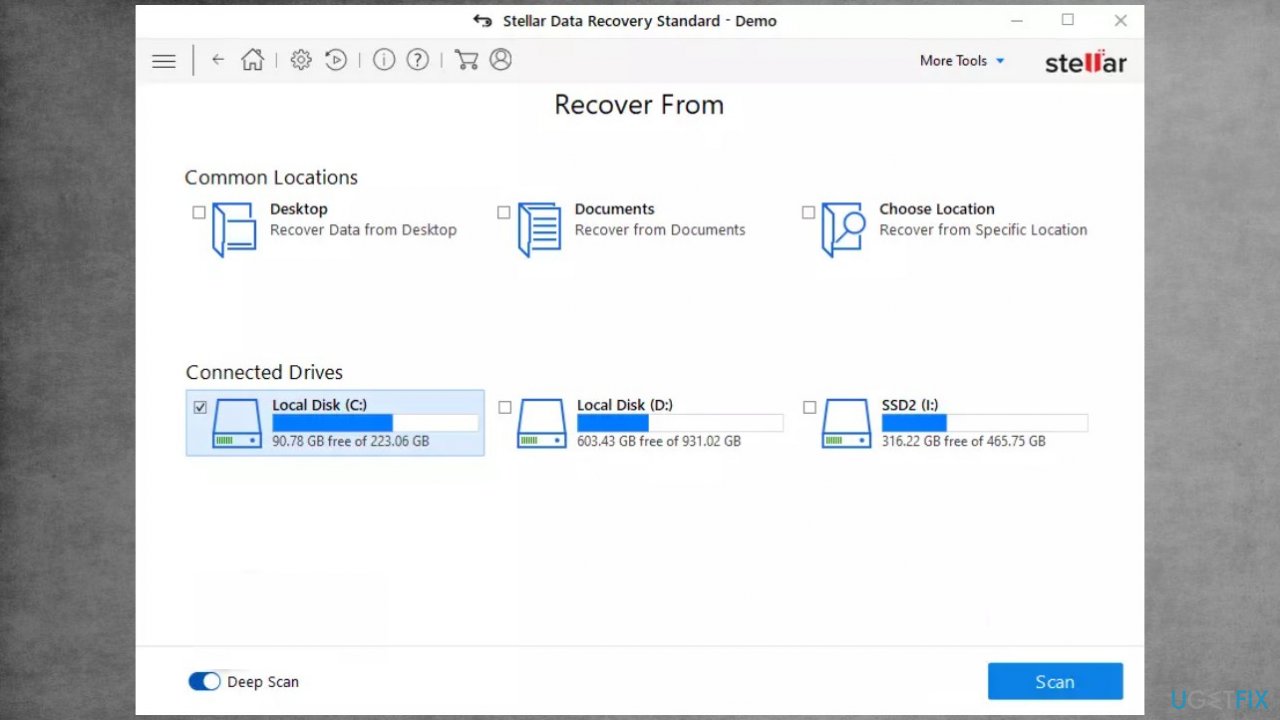
4. Use data recovery software
Try a tool designed for data recovery after such instances. We can recommend Data Recovery Pro.
- Get a tool from a trustworthy source.
- Follow installation instructions.
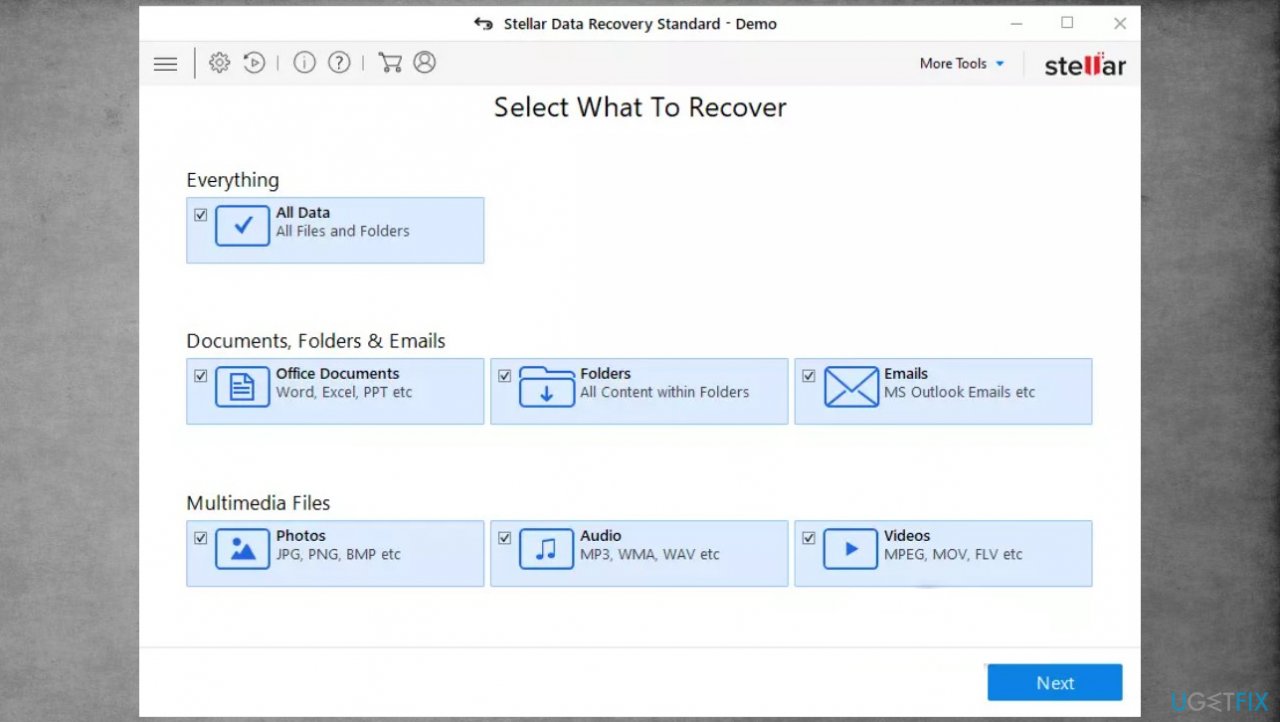
- Once that is finished, use the application.
- Select Everything or pick individual folders to recover.
- Press Next.
- Enable Deep scan at the bottom.

- Pick which Disk you want to be scanned.
- Scan.

- Hit Recover to restore files.
Recover files and other system components automatically
To recover your files and other system components, you can use free guides by ugetfix.com experts. However, if you feel that you are not experienced enough to implement the whole recovery process yourself, we recommend using recovery solutions listed below. We have tested each of these programs and their effectiveness for you, so all you need to do is to let these tools do all the work.
Protect your online privacy with a VPN client
A VPN is crucial when it comes to user privacy. Online trackers such as cookies can not only be used by social media platforms and other websites but also your Internet Service Provider and the government. Even if you apply the most secure settings via your web browser, you can still be tracked via apps that are connected to the internet. Besides, privacy-focused browsers like Tor is are not an optimal choice due to diminished connection speeds. The best solution for your ultimate privacy is Private Internet Access – be anonymous and secure online.
Data recovery tools can prevent permanent file loss
Data recovery software is one of the options that could help you recover your files. Once you delete a file, it does not vanish into thin air – it remains on your system as long as no new data is written on top of it. Data Recovery Pro is recovery software that searchers for working copies of deleted files within your hard drive. By using the tool, you can prevent loss of valuable documents, school work, personal pictures, and other crucial files.
- ^ Josh Fruhlinger. Ransomware explained: How it works and how to remove it. CSOonline. Technology news.
- ^ What Is a Crypto Virus and How Does It Work?. Heimdalsecurity. Cybersecurity reports.
- ^ HELP!! STOP/DJVU Ransomware Virus Attack. Reddit. Online community forum.
- ^ Julie Splinters. Data backup and recovery: why is it important to you. 2spyware. Virus removal guides and spyware news.