Bad Rabbit ransomware is the most aggressive and dangerous computer virus at the moment
WannaCry and Petya are not the only viruses that earned fame during global cyber attacks. Bad Rabbit ransomware, which is suspected to be a new variant of Petya/NotPetya/ExPetr, severely hit Russia, Ukraine, Germany, Turkey and other countries worldwide on October 24th.
The ransomware encrypts all data on the computer and rewrites Master Boot Record. Consequently, the malware restarts the system and then displays a ransom note on the screen. The new malware variant already affected a number of different countries worldwide, and considering how rapidly it spreads, it is a must to know the main facts about it.
The information flow is accelerating, and computer users can quickly get lost as every news site provides more and more details about the virus. Experts from VirusActivity team have prepared a fact sheet about Bad Rabbit cyber attack, what it is and what do computer users need to know.
Top 5 things to know about BadRabbit cyber attack
1. The ransomware spreads via fake Adobe Flash Player updates.
According to experts, developers of the ransomware employed an old and efficient ransomware distribution method that relies of fake Flash Player updates.[1] It appears that hackers injected malicious JavaScript codes into HTML of various websites (most of them are Russian, Bulgarian or Turkish) and this way forced them to serve fake pop-ups suggesting to update an outdated Flash Player.
In case the victim clicks the “Install” button, the malicious script redirects the victim to malware-laden domains and downloads install_flash_player.exe file. At this point, the victim can still step back and delete the downloaded file to avoid a complete data corruption. Unfortunately, execution of the said file starts data encryption process straight away.
The ransomware does not spread using EternalBlue vulnerability as NotPetya virus did. Instead, Bad Rabbit is capable of spreading further via SMB shares.[2]
2. Bad Rabbit is suspected to be an improved variant of Petya/NotPetya ransomware
Speaking of Bad Rabbit’s origins, we must mention the infamous ransomware known as Petya/NotPetya/ExPetr[3]. Both viruses have similarities and differences, but the most noticeable detail is that both of them modify Master Boot Record (MBR) and display a frightening message on a computer screen.
3. The new virus isn’t a wiper and works as a true crypto-ransomware that renders files useless to demand a ransom.
BadRabbit, however, isn’t a wiper. While NotPetya was initially identified as ransomware, further analysis revealed that it corrupted data on the target system permanently. The damage carried by the malicious payload could not be reversed in any way.
The new variant, however, encrypts files with using DiskCryptor utility. Files encoded by Bad Rabbit will have .encrypted file extension appended to their names.
4. The ransomware asks to pay 0.05 Bitcoin
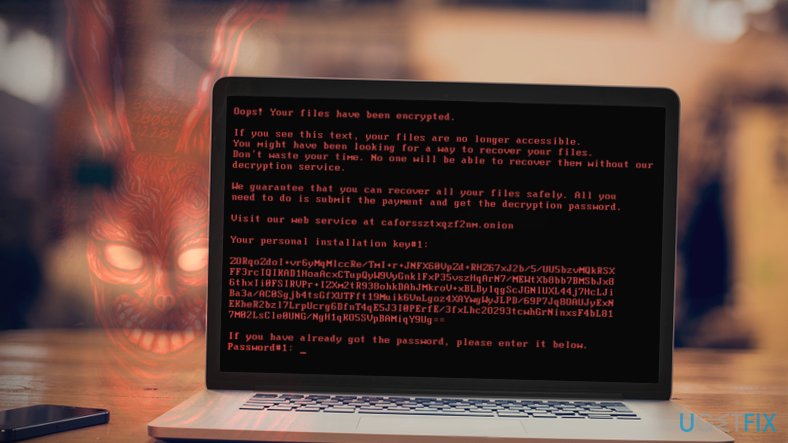
After encrypting the files on the target system, the malware modifies MBR and restarts the computer. As a result, the victims run into a scary-looking message written in red on a black background. The ransomware suggests visiting a suspicious-looking URL that cannot be accessed via regular web browsers.
The victim has to download and install Tor browser to access the payment website. The website then asks entering the personal identification key. Providing the given key allows the victim to see criminals’ Bitcoin address where the payment must be transferred. The ransomware gives 40 hours to complete the transaction. The price of the ransom increases as soon as 40 hours pass.
5. No way to decrypt files encrypted by Bad Rabbit
Unfortunately, no matter how hard you try, there is no way to recover files corrupted by Bad Rabbit malware. There is still some hope left that malware analysts might find a flaw in the ransomware code that could allow them to create a working decryption tool, however, at the moment such expectations seem unrealistic.
Currently, the only possible way to recover files corrupted by this new ransomware variant is to use a data backup.[4] However, firstly you will need to remove Bad Rabbit malware. If you are unfamiliar with the best malware removal tools nowadays, we strongly advise reading reviews on security-related sites such as 2-Spyware.com.
- ^ Marc-Etienne M.Léveillé. Bad Rabbit: Not-Petya is back with improved ransomware. WeLiveSecurity. IT Security Site Covering the Latest News, Research, Cyber Threats and Malware Discoveries.
- ^ Mohit Kumar. Bad Rabbit: New Ransomware Attack Rapidly Spreading Across Europe. The Hacker News. Cyber Security, Hacking News.
- ^ Alice Woods. Another global ransomware attack: Petya or NotPetya?. 2-Spyware. Security and Spyware News.
- ^ Tom Coughlin. WannaCry Ransomware Demonstrates The Value Of Better Security and Backups. Forbes. Global Media Company, Focusing on Business, Investing, Technology, Entrepreneurship, Leadership, and Lifestyle.



