Question
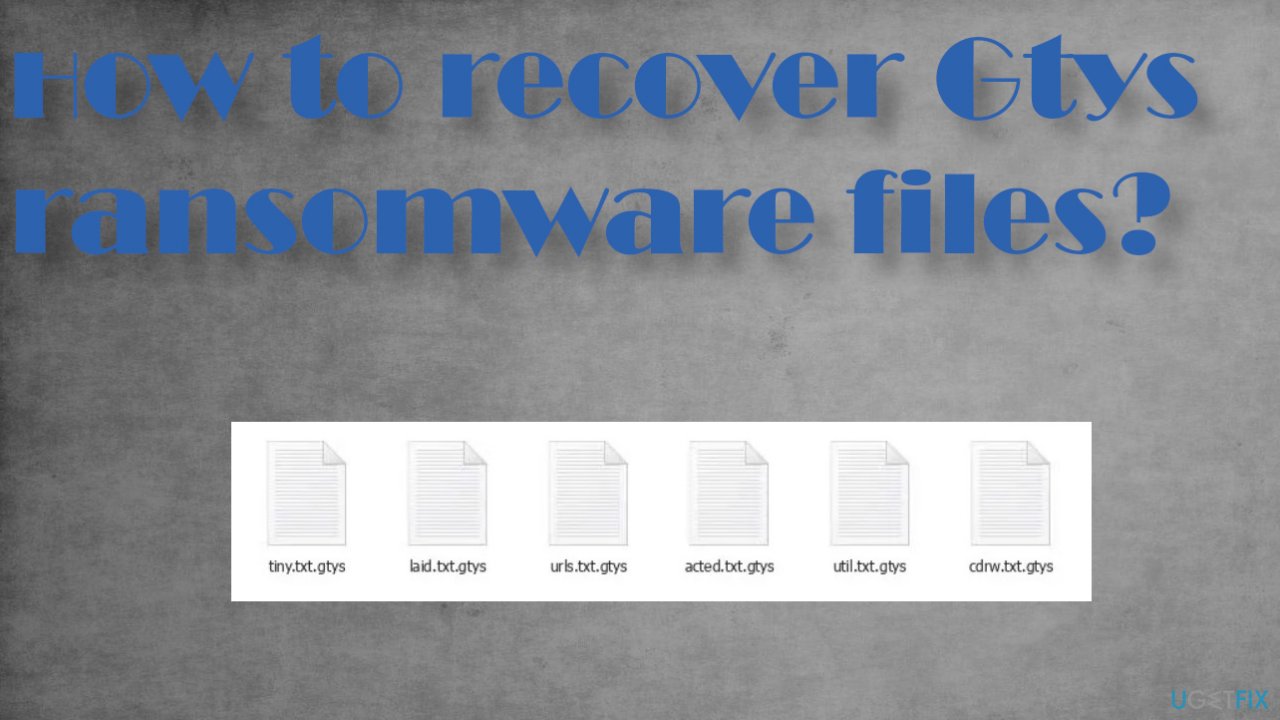
Issue: How to recover Gtys ransomware files?
I need help and serious help here. My all data is encrypted with .gtys. I cannot open any of the images, videos, documents. Many many folders were affected. It is ransomware because I got _readme.txt file with payment instructions. I have no money. No Bitcoins too. Is there any hope for the locked files here?
Solved Answer
The Gtys file virus can be lurking in any data you transmit via pirating platforms or even emails and files in attachments,[1] which is why it's so dangerous. One way this common spreading method function includes – these particular video game cheatcodes, licensed software cracks that are popular and wanted by users.
People want to get software and games and skip through important steps during installations or pay less attention to detail than needed. This is how the threat manages to spread around quickly. This family has been known for years, and it is still very active – releasing versions every few days. This one comes after Udla, Mpag, and Voom.
Demanding money once files get locked
The Gtys ransomware virus creators are relying on fear tactics and false claims about possible decryption methods to make people more eager for a quick payout. They offer 50% off if paid before 72 hours, but their only goal is to get money. It's not surprising that even contacting criminals via [email protected] and [email protected] can be dangerous – they do not care about saving you from malware or recovering your files.
Some of the actors rely on double-extortion methods[2] to keep their options getting money higher. You need to avoid this infection and do not consider payments in exchange for the decryption tool. Stay away from this threat because it's possible that your machine has already been compromised further than encryption.
Unfortunately, there are no official decryption tools for the Djvu ransomware family, so you'll need to rely on alternate methods instead! We have them listed below.
How to recover encrypted files and stop Gtys ransomware?
The data recovery process is not always successful. There are many options for file recovery, but no guarantees that your files will be restored if you pay up these criminals. We'll try our best to list the best possible solutions and alternate approaches in this article, so readers can understand what they might need. However, backups may help more often than people think since most users don't back them daily or weekly like needed.
1. Eliminate the threat
Malware infections are more than just a security threat. They can also be used to carry out functions like data destruction or alterations on the machine. You need to react as soon as possible because once files get locked, and encrypted malware already might be leaving the machine but hiding processes to keep the machine after.
This is why a full system scan is required. After you run the security tool or anti-malware program on the system, any threats will be removed. The AV tool cannot recover lost data because these types of programs detect additional software that is creating crucial issues within our computers and not just damaged pieces.
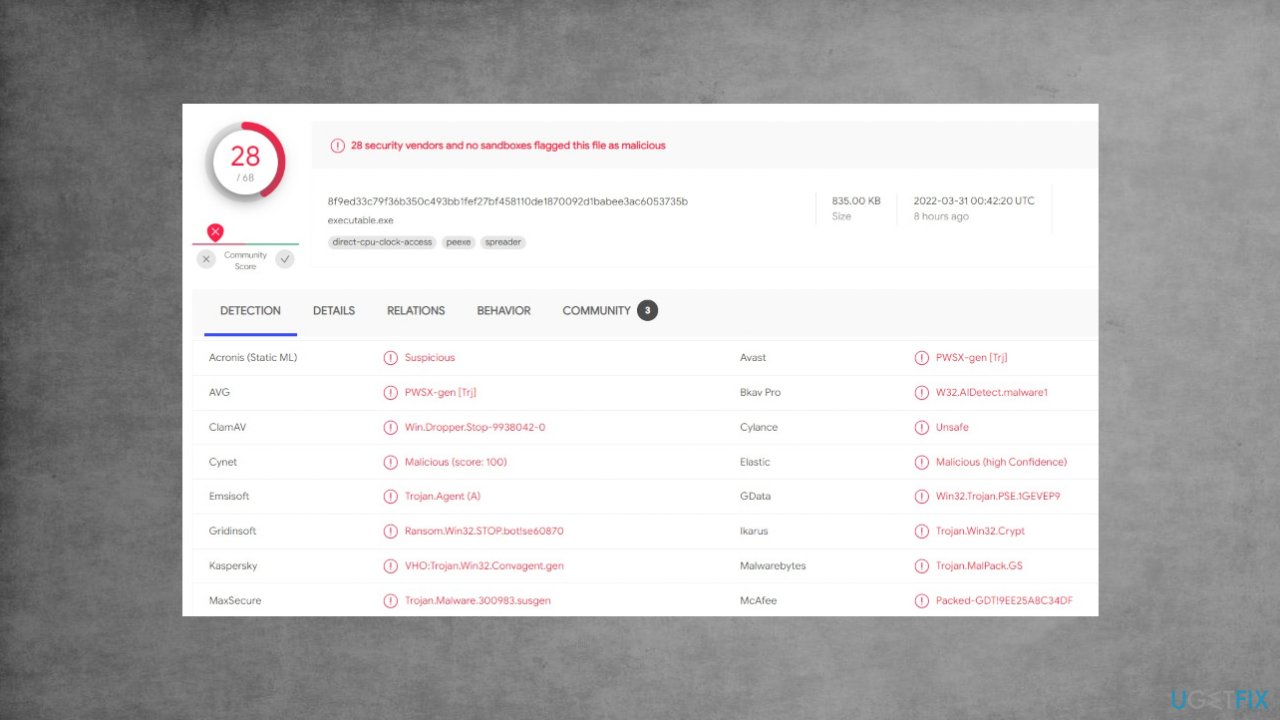
If the Gtys ransomware has infected your device, there are ways to remove it but repairing damaged machine files or even encoded files will not be easy because this kind of malicious software relies heavily on secondary procedures. Rely on removal applications that are based on AV detection.[3]
2. Restore the performance of the machine
If your computer is infected with a malware like Gtys file virus, it will change the way that you interact with system files. For example, an infection could alter the Windows registry database and damage the vital bootup process as well other sections such as deleting or corrupting DLL files which are required for normal operation of the PC. It is crucial to address.
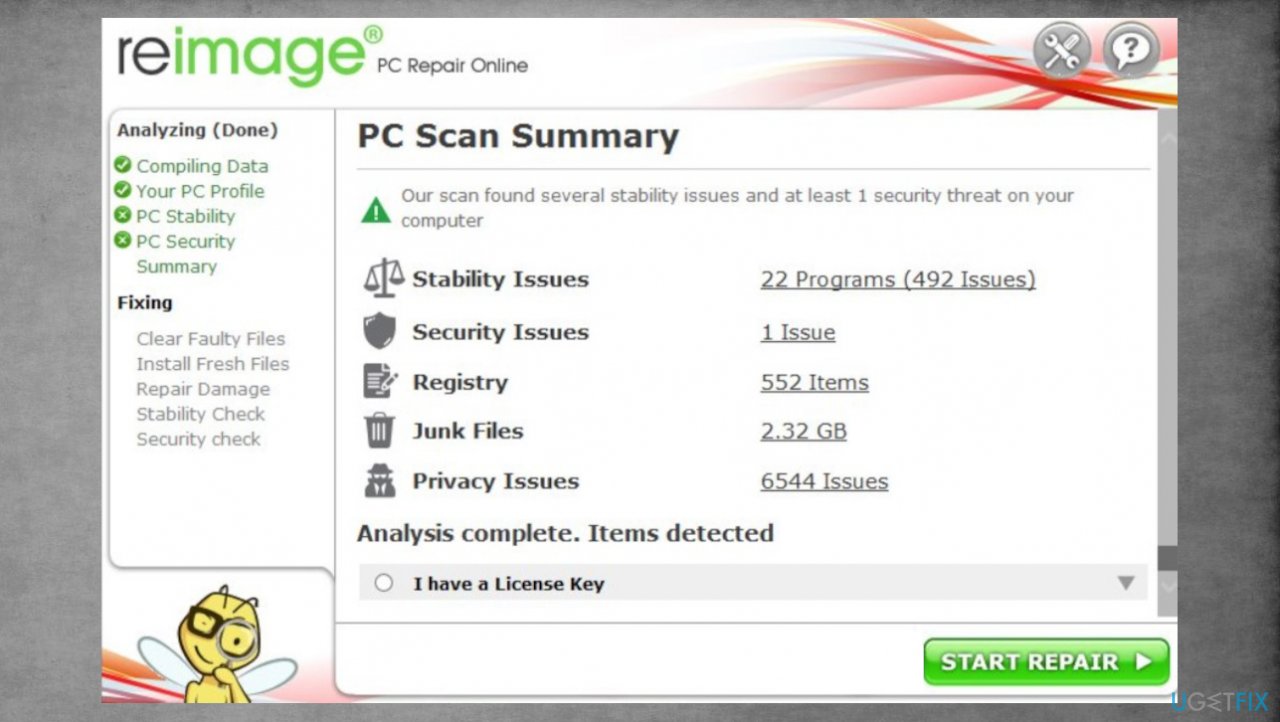
- Download the FortectMac Washing Machine X9 application by clicking on the link.
- Click on the ReimageRepair.exe.
- If User Account Control shows up, select Yes.
- Press Install and wait till the end.
- Once the analysis is completed.
- Check the results in the Summary.

- You can now click on each of the issues and fix them manually.
- If you see many problems that you find difficult to fix- purchase the license and fix them automatically.
3. Try data recovery tools
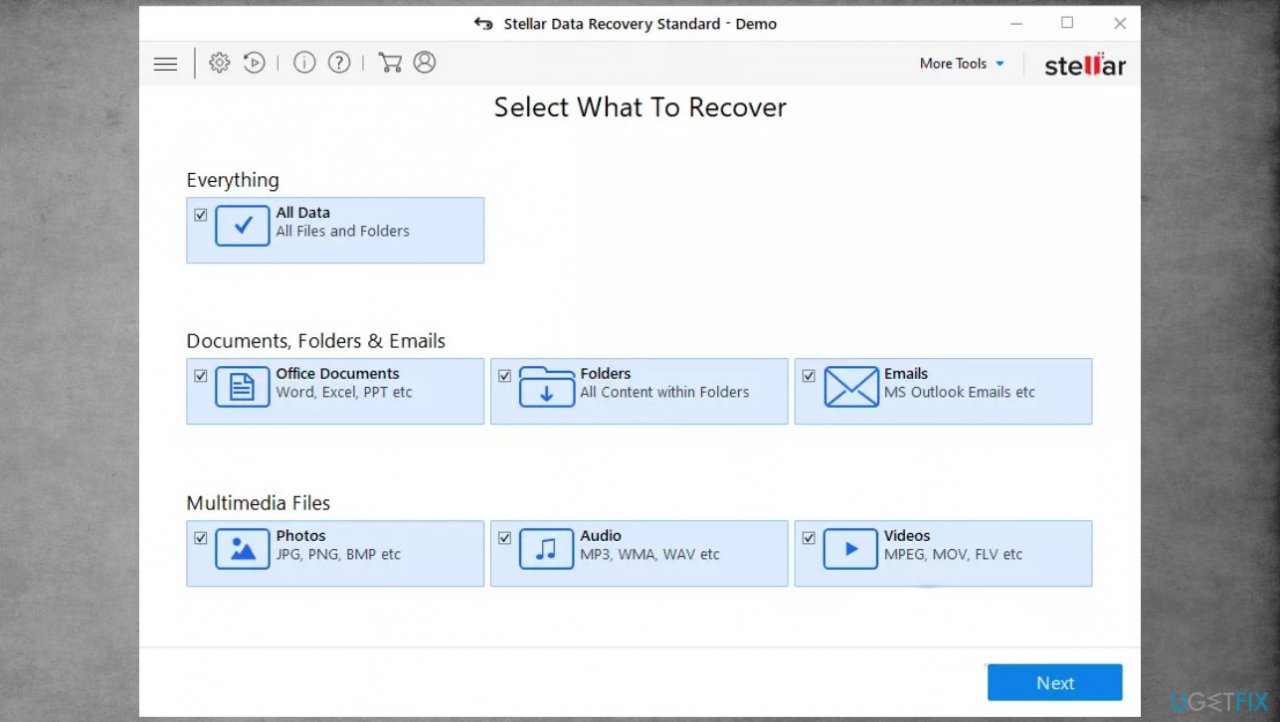
- Get a tool like Data Recovery Pro from a trustworthy source.
- Follow installation.
- Once that is finished, use the application.
- Select Everything or pick individual folders to recover.

- Press Next to continue.
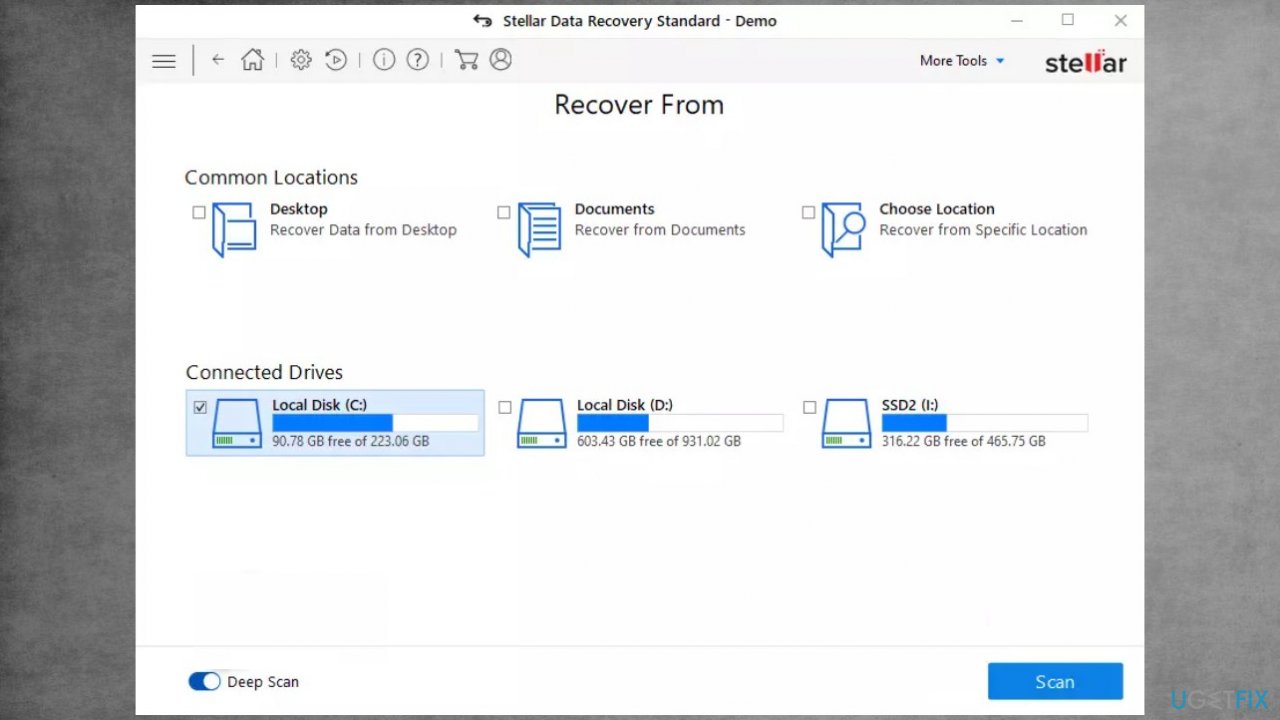
- Enable Deep scan.
- Pick which Disk you want to be scanned.

- Initiate a Scan.
- Hit Recover to restore files.
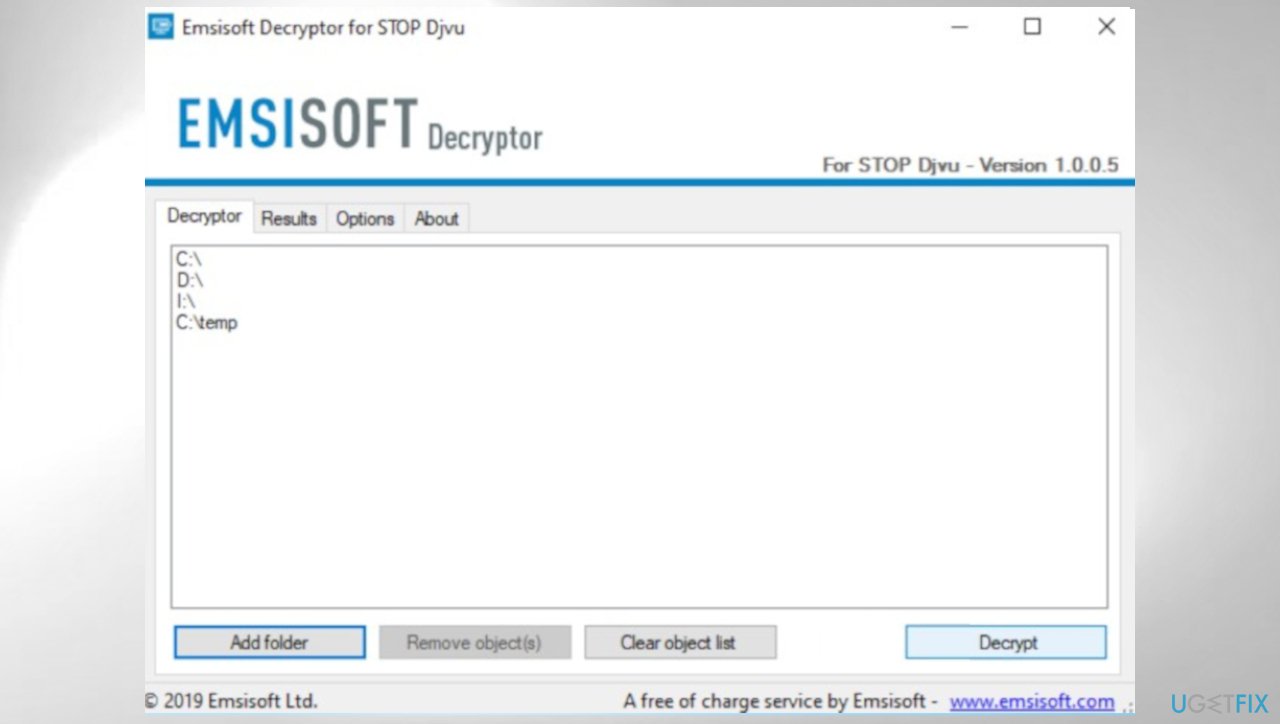
4. Check the decryption option
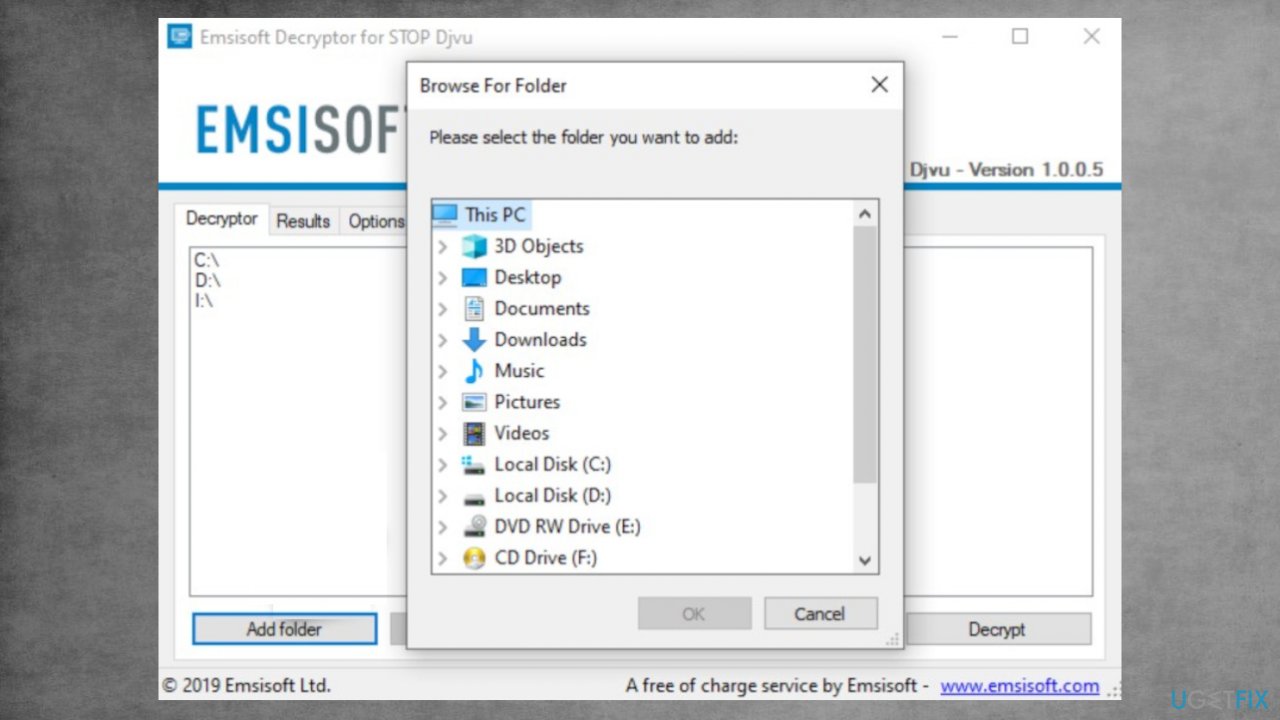
- Download the app on official Emsisoft website.
- Follow the steps of installation on the screen.
- The tool should locate the affected folders.

- You can find them by pressing Add folder at the bottom.
- Press Decrypt.

- There are particular results that can occur indicating if the decryption is possible.
Recover files and other system components automatically
To recover your files and other system components, you can use free guides by ugetfix.com experts. However, if you feel that you are not experienced enough to implement the whole recovery process yourself, we recommend using recovery solutions listed below. We have tested each of these programs and their effectiveness for you, so all you need to do is to let these tools do all the work.
Access geo-restricted video content with a VPN
Private Internet Access is a VPN that can prevent your Internet Service Provider, the government, and third-parties from tracking your online and allow you to stay completely anonymous. The software provides dedicated servers for torrenting and streaming, ensuring optimal performance and not slowing you down. You can also bypass geo-restrictions and view such services as Netflix, BBC, Disney+, and other popular streaming services without limitations, regardless of where you are.
Don’t pay ransomware authors – use alternative data recovery options
Malware attacks, particularly ransomware, are by far the biggest danger to your pictures, videos, work, or school files. Since cybercriminals use a robust encryption algorithm to lock data, it can no longer be used until a ransom in bitcoin is paid. Instead of paying hackers, you should first try to use alternative recovery methods that could help you to retrieve at least some portion of the lost data. Otherwise, you could also lose your money, along with the files. One of the best tools that could restore at least some of the encrypted files – Data Recovery Pro.
- ^ Malicious macro viruses. Wikipedia. The free encyclopedia.
- ^ ‘Double-Extortion’ Ransomware Damage Skyrockets 935%. Threatpost. Virus reports.
- ^ Virus sample analysis. VirusTotal. Online malware scanner.