WannaCry is a serious crypto-malware, which hit the Internet community on Friday, 12 May 2017. Initially, it has been referred to as the Wana Decrypt0r due to the internal name provided on the lock screen. However, security experts soon found out that it has more variant, including Wana Decrypt0r, WannaCryptor, WannaCrypt, Wcry or WNCRY, and it is expected that the variations will keep emerging.
The first WannaCry version, Wana Decrypt0r 2.0, has been detected on May 12, 2017, after hitting the Spanish Telefonica, Portugal Telecom, and NHS Hospitals in England.[1] However, the ransomware did not confine to the organizations and attacked home PCs running older Windows versions, which lack for Microsoft patches indexed as MS17-010, CVE-2017-0146, and CVE-2017-0147.[2] Within a few days, this malicious software managed to infect more than 230,000 computers located in 150 countries, and these numbers make WannaCry align with the most notorious ransomware infections like Locky or Cerber.
WannaCryptor infiltrates the system via the EternalBlue vulnerability, which was detected in Windows Vista, 7, 8, 10 and Windows Server versions. This particular vulnerability has been patched with the MS17-010, CVE-2017-0146, and CVE-2017-0147 security updates, but many PCs skipped the update and left the vulnerability open.
Unfortunately, if the WannaCry ransomware encrypts data (uses AES and RSA algorithms), there is no chance to decrypt files for free. People can pay the ransom for the hackers, recover data using backups or forget about those files.[3]
Update 2018
This virus was considered as an old threat that has been relatively silent, but the third quarter of 2018, news released about WannaCry recent activity and infections all over the world. This cryptovirus has already affected more devices since the current incidents that started in July 2018.
The total amount of blocked WannaCry submissions in Q3 2018, reportedly is 947 027 517 and the activity is discovered in at least 203 countries. The action indicates that this cryptovirus is not dead and the danger is real. Especially, when ransomware attacks increasingly affect big companies and services.[4]
WannaCry also has decryptors developed by various researchers over the year of these attacks. GitHub released decryption tools for various versions, and they might work for new and active threat variants.
WannaCry's success gave the opportunity to copy the tactics
Unfortunately, the huge WannaCry “success” pushed ransomware developers to create and release the copies of the malware. At the moment of writing, security experts registered eight WannaCry copies some of which are in the development phase, while the others have already been released. Thus, be very careful and make sure to protect your PC properly. These are the Wana Decrypt0r copies:
Nr 1. DarkoderCrypt0r
DarkoderCrypt0r encrypts files located on PCs desktop, uses a lock screen similar to WannaCryptor ransomware, required for ransom, and performs all other activities typical for the predecessor. The executable file is named as @[email protected]. All encrypted data get the .DARKCRY file extension and the PC user is urged to pay 300 US dollars ransom. Currently, it uses a HiddenTear code, which means that the files that it encrypts can easily be decrypted.
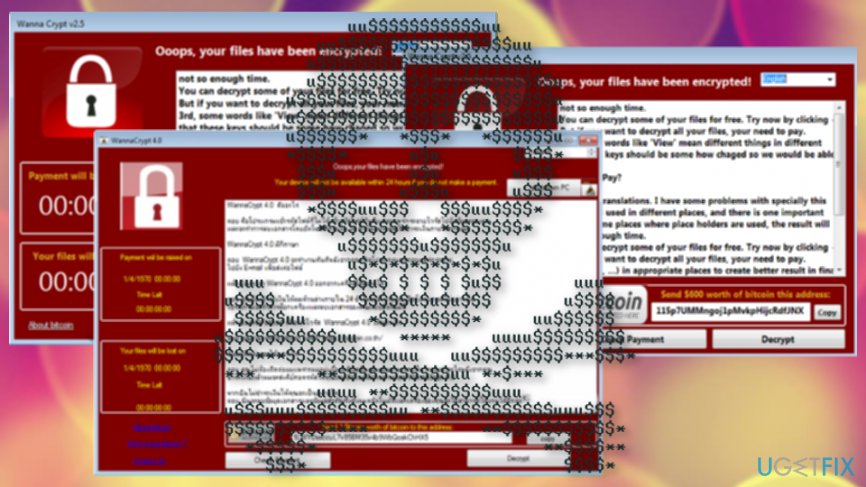
Nr 2. WannaCrypt v2.5
WannaCrypt v2.5 ransomware is currently in development phase. If it infects the PC, it does not lock files, except that it displays the lock screen and requires to pay the 600 US dollars ransom. It is not dangerous yet but can scare people to death.
Nr 3. WannaCrypt 4.0
WannaCrypt 4.0 is yet another WannaCry virus copy, which can be classified as non-malicious yet. It spreads just like any other ransomware virus, except that it does not encrypt files. The ransom note, lock screen, and other information are provided in the Thai language, meaning that it will target Thailand users.
Nr 4. Aron WanaCrypt0r 2.0 Generator v1.0
Aron WanaCrypt0r 2.0 Generator v1.0 is referred to as a customizable WannaCry Ransomware generator. It allows people to select the text, colors, images, font, and other settings of WannaCry lock screen. It is speculated that hackers are also using the Wana Decrypt0r executable and spreading it to generate the ransom. Luckily, this “service” is not yet available. People can only generate a customized WannaCry lock screen, but the ransomware executable is not spread.
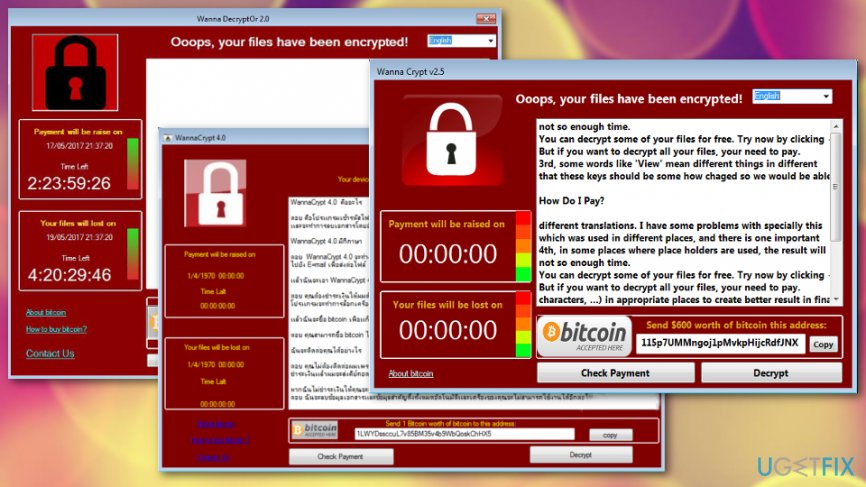
Nr 5. Wana Decrypt0r 2.0
The Wana Decrypt0r 2.0 executable is MS17-010.exe. The lock screen and ransom note is similar to the WannaCry. The Indonesian version of the virus is available.
Nr 6. @kee
@kee ransomware encrypts personal files and provides a ransom note inside a“Hello There! Fellow @kee User!.txt“ file.
Nr 7. WannaDecryptOr 2.0
WannaDecryptOr 2.0 hasn’t yet been fully developed. It is capable of infecting computers, but cannot encrypt files. Besides, it’s lock screen, and ransom note does not provide information about the virus and instructions on how to pay the ransom. Nevertheless, it’s crucial to uninstall the virus because it may be updated shortly and encrypt the files afterward.
Nr 8. Wanna Subscribe 1.0
Not much information received yet. This is a threat written in Java and has the grey-colored design of a previously known ransom window.
As you can see, WannaCry virus has many clones, some of which are already distributed and the others are in the development phase. However, it’s critical to update and secure your PC properly. In this and this posts, you can find information on what precautionary measures should be taken to protect yourself from WannaCry attack and what steps should be taken if your PC has already been infected. Taking these preventive measures, you will protect the system from all WannaCry variants, including its imitators.
- ^ Lizzie Dearden . NHS to spend £150m on cyber security to bolster defences after WannaCry attack. Independent. UK and worldwide news.
- ^ WannaCry Ransomware Vulnerability (CVE-2017-0143). Lexmark. Print, secure and manage your information.
- ^ Shaun Nichols. Less than half of paying ransomware targets get their files back. Theregister. Tech news for the world.
- ^ Matthew Wall and Mark Ward. WannaCry: What can you do to protect your business?. BBC. Breaking news.



