Web security consultant found Facebook vulnerability uncovering friend lists and credentials
Facebook is one of the most widely used social media platforms on the Internet and a web security consultant, J. Franjkovic, has detected a massive vulnerability on October 6, 2017, which exposes friend lists despite the privacy settings of the user. It means that any hacker can circumvent the system and see all friends of any Facebook user.
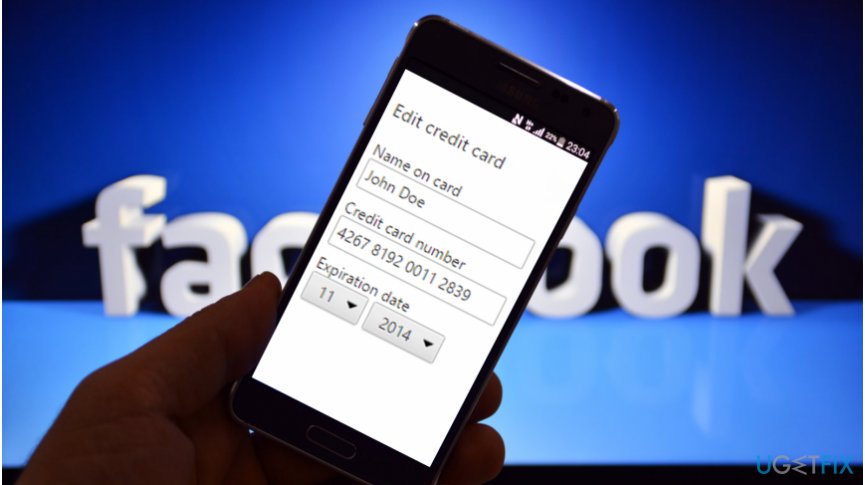
Additionally, earlier, the researcher has also found a Facebook bug allowing to gain various details of payment cards used by people on the social networking platform. The vulnerability was discovered on February 23, 2017, and helped the researcher to receive the credentials of any user on Facebook.
Facebook flaw exposed the first six digits of the card which help identify the bank that has provided it[1]. Also, the security consultant managed to get the last four digits of the payment card, cardholder's first name, card type, ZIP code, country, expiry month and date as well.
The researcher bypassed whitelisting mechanism
J. Franjkovic said that there is a way to disclose the friend list by using GraphQL[2] queries and the client's token[3] from Facebook-developed applications. The researcher managed to bypass whitelisting mechanism by using “doc_id” instead of “query_id” and the access_token from Facebook for Android app.
Once the whitelisting[4] mechanism was circumvented, J. Franjkovic sent GraphQL queries. While most of them revealed only the data which is already public, CSPlaygroundGraphQLFriendsQuery exposed the hidden friend list of any user on Facebook whose ID was included.
Similar to the latter bug, another one was also related to GraphQL and helped to obtain credit card details. The researcher also used user's ID from victim's Facebook account and the access_token which can be taken from the Facebook app for Android.
J. Franjkovic describes this Facebook vulnerability as a textbook example of an insecure direct object reference bug, also known as IDOR[5]:
This is a textbook example of an insecure direct object reference bug (IDOR).
Facebook fixed the bug within several hours
Facebook team's reaction to the report about the existing vulnerability surprised the web security consultant. The researcher received a response about the possibility to leak friend lists after less than a week, on October 12. IT experts have fixed the bug on October 14 and blocked the bypass of whitelisting mechanism on October 17, 2017.
While the response to the report about credit card information leak was received after less than 40 minutes and the vulnerability was eliminated after 4 hours and 13 minutes.
- ^ David Addison. Anatomy of a credit card number and the utility of the BIN. Dirigodev. Marketing, Modern Responsive Web Design & Scalable.
- ^ GraphQL. Wikipedia. The Free Encyclopedia.
- ^ Token. TechTarget. Computer Glossary, Computer Terms.
- ^ Whitelist. The Tech Terms. Computer Dictionary.
- ^ Josip Franjkovic. Getting any Facebook user's friend list and partial payment card details. Josip Franjković. Personal website.



