Question
Issue: How to Decrypt .WNCRY File Extension Files?
I have Windows OS, and recent news about WannaCry malware is a bit alarming. Is there any way to decrypt files having .wncry file extensions or is it a complete dead-end?
Solved Answer
WannaCry ransomware or alternatively labeled as .wncry file extension virus has started rampaging on May 17, 2017. Despite speculations about the origin of the malware, recent evidence reveals that it might have been developed in Malaysia. While IT cyber security forces have managed to limit its scale of the attack, the malware is still at its early distribution stage. During the weekend, the cyber assault encompassed more than 150 countries, more than 230 000 infected devices. The cause of the rampage was the leak of NSA hack tool based on EternalBlue or CVE-2017-0145 vulnerability. This flaw facilitates the hijack faster infection of SMBv1 servers. Though Microsoft issued patches for this flaw already in March, the number of infected devices reveals that both users and companies still do not update operating systems regularly.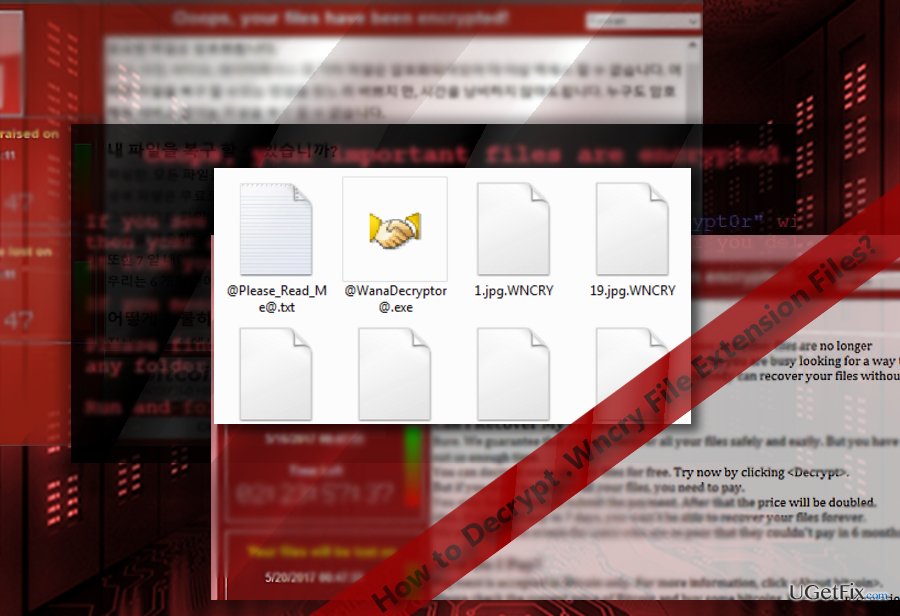
On the other hand, perhaps WannaCry, Wana Decrypt0r or WanaCrypt0r would have never been developed, if not the NSA data theft. The latter organization was aware of this vulnerability. On the other hand, it again sparks theories that the latter agency might have exploited the vulnerability for its own purposes as the flaw makes all outdated Windows OS versions vulnerable to the attack. EternalBlue creates a backdoor door for the malware to occupy the device. After the infection process is finished, the malware launches its window. Furthermore, its computer worm specifications grant the virus ability to corrupt all available devices on the same server or network. Therefore, it resulted in a worldwide scale attack. Interestingly, that the malware ransom note does not indicate any information about the encryption method. As common for crypto-malware, the penetrators alert users to transmit the money within three days from the infection. Otherwise, the amount of the demanded money doubles. If victims fail to remit the payment within a week, the files are supposedly deleted. However, such psychological pressure is a popular strategy among hackers, so even if this menace enters the system, there is no guarantee that the penetrators play fairly.
Prevention methods
Unlike other samples of ransomware category, this malware does not attack simply via spam emails. As previously mentioned, it makes use of EternalBlue which grants secret access to the computer. In other words, it creates a backdoor. Amid the reports of this malware worldwide, Microsoft has issued an urgent update. In case, you did not receive it, check for the updates manually and install the ones which were not installed automatically or failed due to a temporal error. In addition, update your security applications. You can check your system with FortectMac Washing Machine X9 or MalwarebytesAnti-Malware.
Decrypting .wncry file extension files
Note that before you attempt to decrypt files, complete .wncry file virus removal. The hackers offer you to install their own Wana Decryptor. However, after installing the software, there is a chance that it might inflict even more damage in the future. Dealing with hackers is never a good solution. You may attempt decrypt data with the assistance of Data Recovery Pro program or Shadow Explorer. The latter uses shadow volume copies to restore files. This method is effective in case the malware does not delete files in advance. For more information how to use these programs, take a look at the guides provided in the links.
Recover files and other system components automatically
To recover your files and other system components, you can use free guides by ugetfix.com experts. However, if you feel that you are not experienced enough to implement the whole recovery process yourself, we recommend using recovery solutions listed below. We have tested each of these programs and their effectiveness for you, so all you need to do is to let these tools do all the work.
Access geo-restricted video content with a VPN
Private Internet Access is a VPN that can prevent your Internet Service Provider, the government, and third-parties from tracking your online and allow you to stay completely anonymous. The software provides dedicated servers for torrenting and streaming, ensuring optimal performance and not slowing you down. You can also bypass geo-restrictions and view such services as Netflix, BBC, Disney+, and other popular streaming services without limitations, regardless of where you are.
Don’t pay ransomware authors – use alternative data recovery options
Malware attacks, particularly ransomware, are by far the biggest danger to your pictures, videos, work, or school files. Since cybercriminals use a robust encryption algorithm to lock data, it can no longer be used until a ransom in bitcoin is paid. Instead of paying hackers, you should first try to use alternative recovery methods that could help you to retrieve at least some portion of the lost data. Otherwise, you could also lose your money, along with the files. One of the best tools that could restore at least some of the encrypted files – Data Recovery Pro.


