Question
Issue: How to Protect Your Computer from Bad Rabbit Ransomware?
Hello. I am afraid of Bad Rabbit ransomware attack as my kids always play various computer games and download whatever the Internet has to offer. Can you provide a tutorial on how to set up a trustworthy computer security system so that the virus could not encrypt files on my disks? I already heard of backups as an option, but maybe there are other options?
Solved Answer
Bad Rabbit ransomware (a suspected variant of Petya 2017/NotPetya) is one of the most fearsome data-encrypting viruses at the moment. It primarily attacked Russia and Ukraine as well as Turkey and Bulgaria, but other countries are among the targets as well. The ransomware is also known as DiskCoder.D and it spreads in the form of a fake Flash Player Update that appears on websites compromised by hackers.

Once installed on the system, the virus encodes all data with a combination of AES-256-CBC and RSA-2048 ciphers. [1] Following a successful encryption, the malware changes Master Boot Record[2] and restarts the computer. Also, we must point out that Bad Rabbit virus attempts to spread via SMB shares, trying to infect as many computers on the network as possible.
The malicious virus then displays a message on a black computer’s screen, telling the victim about the cyber attack which turned all victim’s files useless. Bad Rabbit demands the victim to visit a particular website via Tor browser to access data recovery solutions.
After installing the aforementioned browser and entering the provided address along with personal identification key provided by the ransomware, the victim gets access to criminals’ Bitcoin address. This address is the one where the victim is supposed to send the money to. At the moment, the malware demands 0.05 bitcoin as a ransom, which is more or less $280. Since Bitcoin value changes all the time, we believe that the price will go up shortly.
Speaking of ways to protect your computer from the described virus, we have provided a tutorial on how to create your own vaccine[3] against Bad Rabbit ransomware attack which will prevent the virus from encoding your files. Follow the steps given below, and the fearsome malware variant won’t encrypt your files.
Protect your Computer from Bad Rabbit virus attack
Method 1. A Guide on How To Create a Vaccine for Bad Rabbit Ransomware
- First of all, go to C:\\Windows folder. In this folder, you need to create an infpub.dat and cscc.dat file. A quick way to create both files is via Command Prompt (with Administrator’s rights).
- Open Start menu and use the search box to find Command Prompt (just type the name of the program into the search box). Right-click on the matching result and choose Run as administrator.

- You will be asked to provide your admin’s password in order to continue. Do as the computer requires and then you will get access to the Command Prompt (Admin mode).
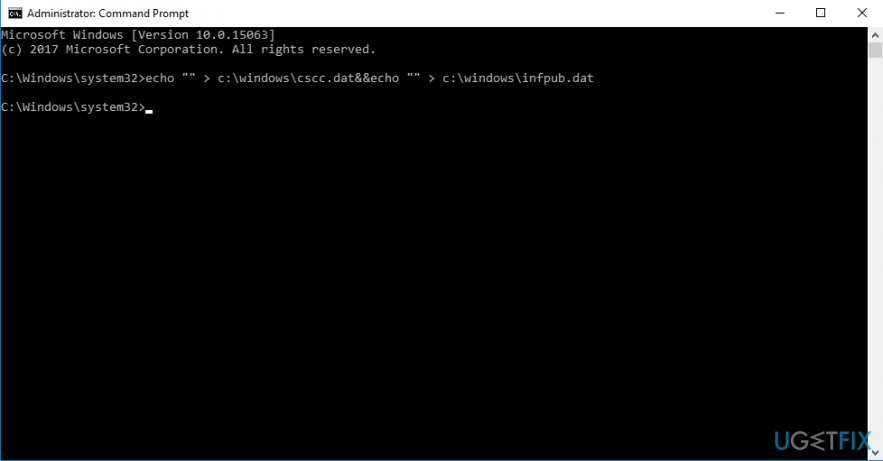
- Once the CMD window appears, type the following commands and press Enter:
- echo “” > c:\\windows\\cscc.dat&&echo “” > c:\\windows\\infpub.dat

- echo “” > c:\\windows\\cscc.dat&&echo “” > c:\\windows\\infpub.dat
- You won’t see any pop-ups or information messages after entering this line into Command Prompt. Do not worry; the next step is to go to My PC (or My Computer), then to C:\\ disk, and then to Windows folder. Here, you will find cscc.dat and infpub.dat files. You can check their creation date to be sure that these are the files you just created. Next, you will need to modify their properties.
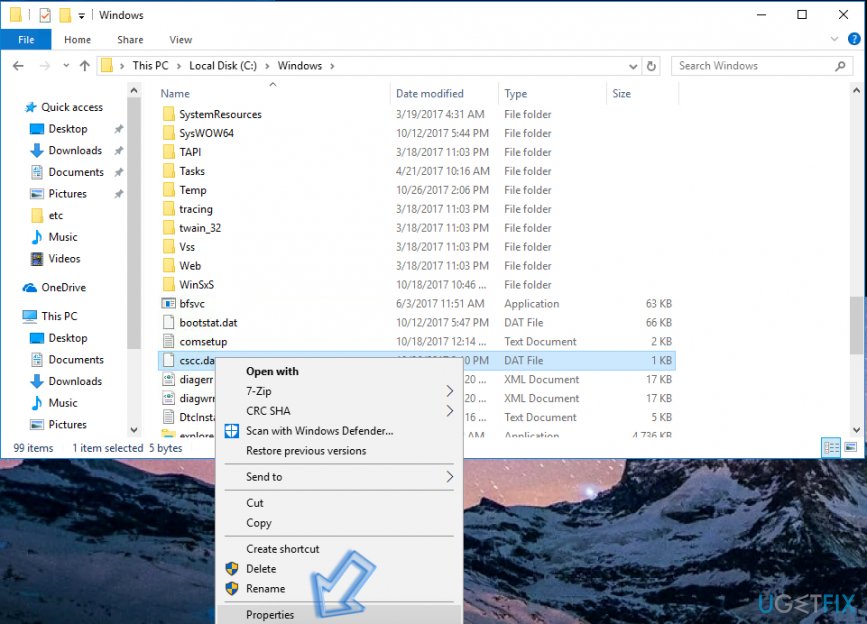
- Right-click on the cscc.dat file and choose Properties from the list.

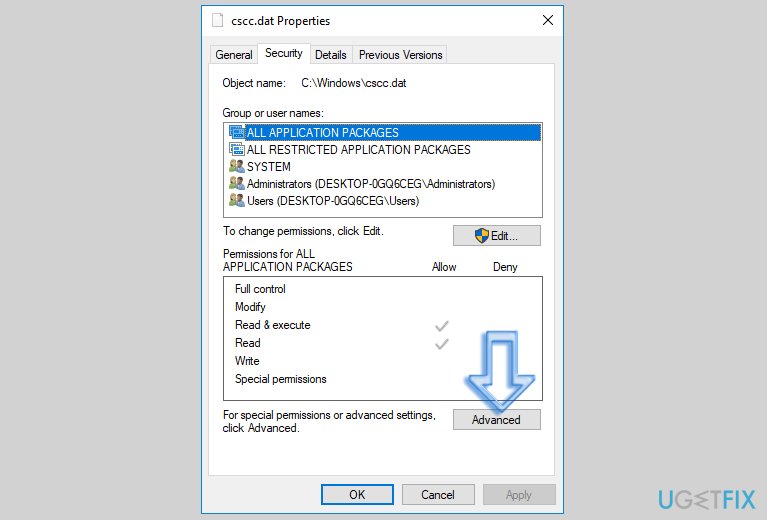
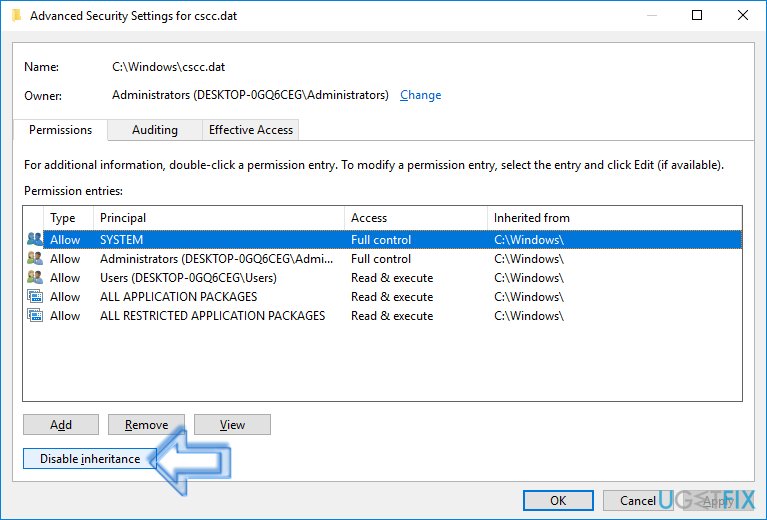
- Click to open Security tab and then choose Advanced option.

- Here, select SYSTEM option and click Change Permissions. You might be asked to enter Admin’s password once again.
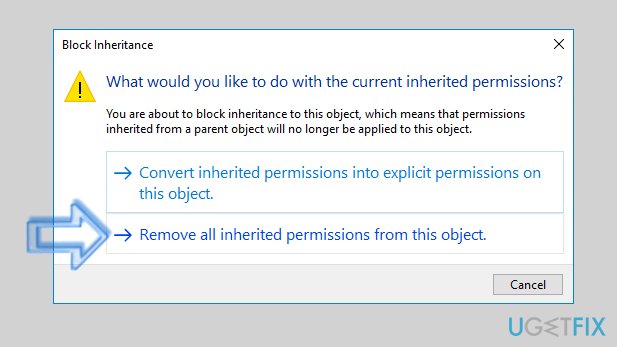
- In the next Window, you should click Disable inheritance button.

- Next, click Remove all inherited permissions from this object.

- If you are using an older version of Windows, you might just need to deselect the checkbox next to Include inheritable permissions from this object’s parent and click Remove in the “Windows Security” pop-up that appears on the screen.
- Click Apply and OK when closing the settings panels.
- Now, repeat the same steps with the infpub.dat file which you also created in C:\\windows directory.
Method 2. Create a Data Backup
The second thing that you must do in order to keep your files safe and sound is to create a backup for them. To create a backup, you will need an external data storage device (USB, DVD, portable hard drive.
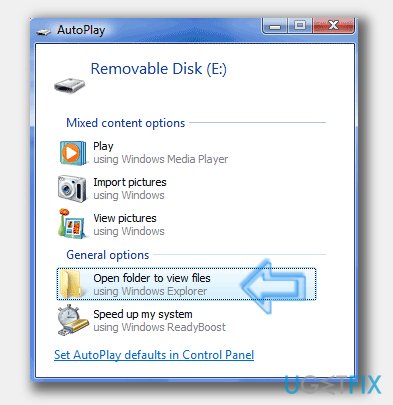
- Plug in the device to your computer.
- Once AutoPlay window appears, select Open Folder to View Files.

- The folder that appears on the screen is the place where you need to paste data copies that you want to protect. Simply search your computer for files that are important to you, copy them and paste them into the folder that belongs to the external drive you just plugged into your computer.
- Wait until all files are copied safely.
- In Windows menu tray, click on the small arrow pointing upwards and find Safely Remove Hardware and Eject Media icon (it looks like USB cable with a tick in a green circle next to it). Right-click on it, find your device and select Eject [your device name].
- Remove the backup and store it in a safe place.
Method 3. Protect your computer using anti-malware software.
If you take computer protection seriously, you should get a reliable security software to protect your computer from malicious programs at all times. If you are using an antivirus already, update it and also increase the security levels by installing anti-spyware and optimization software like [ref if=”Reimage”].
Method 4. Keep your software up-to-date
When trying to protect your computer from malware, it is important to remember that security vulnerabilities in outdated programs allow installation of various computer infections. Sometimes all that it takes to get infected is merely to visit a compromised domain or click on malware-laden ads. Therefore, never delay updates that your Windows computer suggests installing.
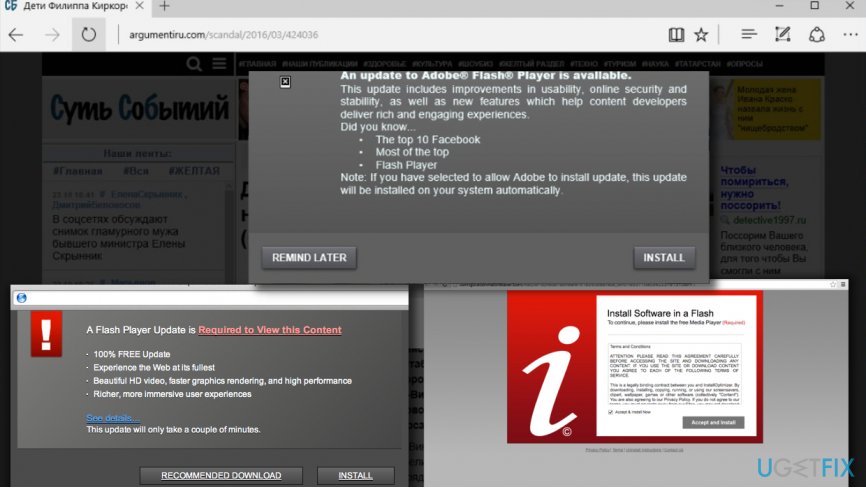
Method 5. Avoid installing Adobe Flash Player updates from unknown sites
Cybercriminals can deceive you by pushing deceptive software updates which seem useful at first sight. In reality, you should stay away from pop-up ads suggesting software updates and install them ONLY from websites that belong to developers of that particular software. For example, if you need to update Adobe Flash Player, visit Adobe website. Below, you can see some examples of deceptive Adobe Flash Player ads.[4]
Method 6. Never open questionable email attachments
Hackers tend to send out myriads of fake messages to people around the world and attach malicious files to them. While the majority of such letters get stuck in your email service provider’s “Spam” filters, some of them manage to get through. We want to advise you to stay away from suspicious messages you receive into your Inbox.
Even if the message looks legitimate, but you did not expect to receive it – better bypass it. The 2-spyware team has provided a great guide on how to identify malware-laden emails – we suggest checking it out.
Optimize your system and make it work more efficiently
Optimize your system now! If you don't want to inspect your computer manually and struggle with trying to find issues that are slowing it down, you can use optimization software listed below. All these solutions have been tested by ugetfix.com team to be sure that they help improve the system. To optimize your computer with only one click, select one of these tools:
Protect your online privacy with a VPN client
A VPN is crucial when it comes to user privacy. Online trackers such as cookies can not only be used by social media platforms and other websites but also your Internet Service Provider and the government. Even if you apply the most secure settings via your web browser, you can still be tracked via apps that are connected to the internet. Besides, privacy-focused browsers like Tor is are not an optimal choice due to diminished connection speeds. The best solution for your ultimate privacy is Private Internet Access – be anonymous and secure online.
Data recovery tools can prevent permanent file loss
Data recovery software is one of the options that could help you recover your files. Once you delete a file, it does not vanish into thin air – it remains on your system as long as no new data is written on top of it. Data Recovery Pro is recovery software that searchers for working copies of deleted files within your hard drive. By using the tool, you can prevent loss of valuable documents, school work, personal pictures, and other crucial files.
- ^ Marc-Etienne M.Léveillé. Bad Rabbit: Not-Petya is back with improved ransomware. WeLiveSecurity. News, Views, and Insight from the ESET Security Community.
- ^ Bad Rabbit virus debuts during third major global cyber attack of 2017. Virus Activity News. The Latest News about Malware and Spyware.
- ^ Lital Asher-Doman. Cybereason researcher discovers vaccine for Bad Rabbit ransomware. CyberReason Blog. IT News, Security Tips.
- ^ Matt Burgess. The Bad Rabbit malware was disguised as a Flash update. WIRED UK. Future Science, Culture & Technology News and Reviews.