Question
Issue: How to Use Rannoh Decryptor?
My PC’s has been encrypted by Cryp1 and I need help recovering my files! My friend has given me Rannoh Decryptor on the flash drive, but I have no idea how to use it… Could you please provide me with some quick software usage guide or something?
Solved Answer
Ransomware are really devastating programs as they may damage your personal files beyond the point of recovery. These parasites use strong encryption algorithms to render files unreadable. Typically, the encryption is uncrackable, and the virus experts can only rely on the virus developers to leave errors in other parts of the ransomware code.
Luckily, in most cases, malicious programmers do leave gaps that can be used to decrypt the virus. Kaspersky is one of the companies that works on ransomware decryption intensively and has already released a number of different decryptors for CoinVault, Bitcryptor, Wildfire, Rakhni, Chimera, Crysis and Jaff.
The famous endpoint security company has especially cheered up ransomware victims after they released Rannoh Decryptor, a tool capable of decrypting files affected by AutoIt, Cryakl, Crybola, CryptXXX, Cryp1, Rannoh, Fury and Polyglot (Marsjoke).
While the mentioned ransomware viruses are still actively spreading throughout the web, their victims are still looking for instructions explaining how to use Rannoh Decryptor. In this article, we will try to answer this question as comprehensively and concisely. Keep reading and you will learn how to perform the data recovery safely.

Recovering encrypted file using Rannoh Decryptor:
Step 1. System cleanup
You cannot start data recovery without cleaning up your computer from the ransomware that has been fully eliminated from the computer first. It is absolutely necessary to make sure that no ransomware files are left on the device to potentially interfere with the data recovery.
Please note that leaving random virus files on your computer can cause the ransomware to bounce back to the PC and repeatedly encrypt the files. To be sure that none destructive virus components are left on the system, scan your device with Reimage or similar antivirus software.
Step 2. Data backup
Normally, professional companies that invent ransomware decryption tools make sure that these programs are well-built and pose no danger to the user’s’ personal files. Nevertheless, it may be an accidental mistake on the users’ end that may trigger data destruction. That is why before commencing with the data recovery it is recommended to save backup copies of the encrypted files on a location separate from the device on which the recovery operation will take place.
Software like CryptoSearch can speed up the process of data recovery quicker as it automatically separates encrypted files from non-encrypted ones.
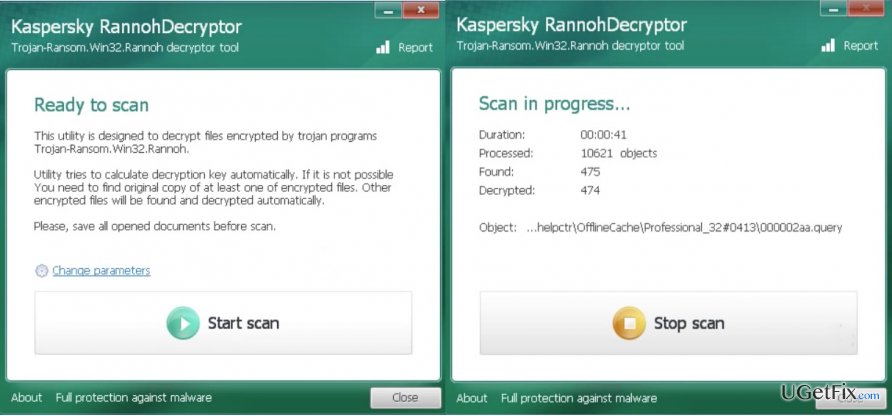
Step 3. Data recovery using Rannoh Decryptor
- You can downlaod Rannoh Decryptor on Kaspersky’s official website. Nevertheless, to save you some time, we have included quick download link here: Download RannohDecryptor.zip
- After the download is finished, launch Rannoh Decryptor on the computer that you want to decrypt
- In the Decryptor Window click the Start scan button

- Before the program starts scanning your device, it will ask you to provide a path to one encrypted and one non-encrypted version of some document. Make sure you have these two samples prepared before the scan
- After the scan is done, you may delete the encrypted version of the files by selecting the Delete encrypted files after decryption option
- Reset your computer to save changes.
Recover files and other system components automatically
To recover your files and other system components, you can use free guides by ugetfix.com experts. However, if you feel that you are not experienced enough to implement the whole recovery process yourself, we recommend using recovery solutions listed below. We have tested each of these programs and their effectiveness for you, so all you need to do is to let these tools do all the work.
Protect your online privacy with a VPN client
A VPN is crucial when it comes to user privacy. Online trackers such as cookies can not only be used by social media platforms and other websites but also your Internet Service Provider and the government. Even if you apply the most secure settings via your web browser, you can still be tracked via apps that are connected to the internet. Besides, privacy-focused browsers like Tor is are not an optimal choice due to diminished connection speeds. The best solution for your ultimate privacy is Private Internet Access – be anonymous and secure online.
Data recovery tools can prevent permanent file loss
Data recovery software is one of the options that could help you recover your files. Once you delete a file, it does not vanish into thin air – it remains on your system as long as no new data is written on top of it. Data Recovery Pro is recovery software that searchers for working copies of deleted files within your hard drive. By using the tool, you can prevent loss of valuable documents, school work, personal pictures, and other crucial files.