Question
Issue: How to enable two-factor authentication on Gmail?
Could you explain to me how to turn on two-factor authentication on Gmail account?
Solved Answer
Two-factor authentication, also known as 2FA,[1] TFA or two-step verification, is one of the methods to add more security to your personal information online. Once you set it up, you have to enter your login, password, and verification code that is being sent to your mobile device or authentication app in order to access your account.
You can enable two-factor authentication on Gmail, Facebook, Twitter, Reddit and many other online services. Users are advised[2] to turn on this feature as prevention of data breaches and other unauthorized access to your account if some evil-minded people guess your password.
If someone gets access to your account,[3] they might send emails on behalf of you, steal your contact list or get access to your other accounts. For instance, criminals might reset your banking account password. There's no doubt that this may lead to serious problems.
Therefore, two-factor authentication gives an extra layer to cyber security. Google allows enabling this feature on all its services, including Gmail, Drive, G+, YouTube, and others. Though, it’s impossible to set 2FA for Gmail only. You will need to protect all Google account.

Instructions how to enable two-factor authentication on Gmail and Google
As you already know, you can set 2-step verification on Gmail by enabling this feature on Google account. Therefore, every time you want to access your Gmail, YouTube or other Google account, you will need to confirm your login as soon as you enter your password.
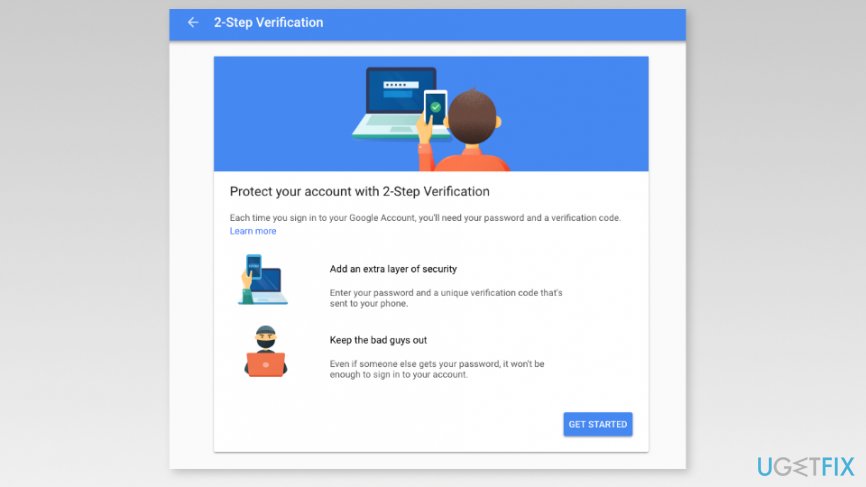
- Access 2-Step Verification page using a web browser on the computer and click “Get started” button.

- Sign in to your Google account.
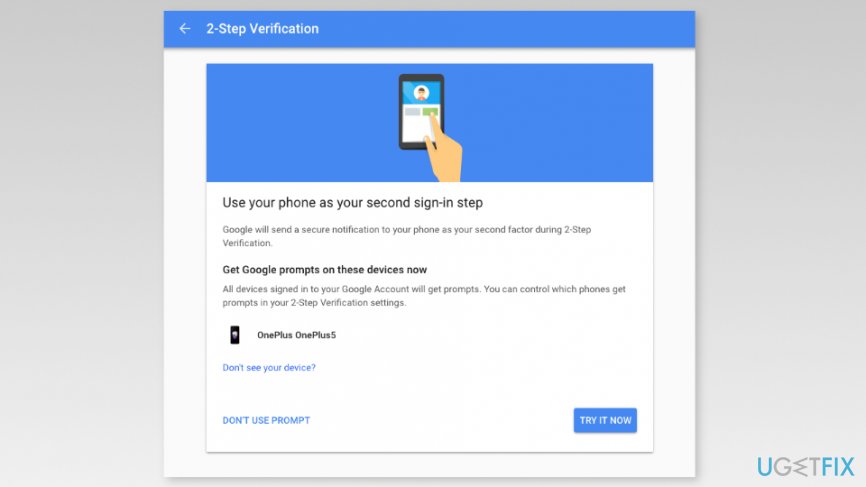
- Once you log in, you will be offered to set your phone as a second sign-in step. If you have logged in to your Google account using your mobile phone, you will see it under device list. Click “Try It Now” button to proceed.

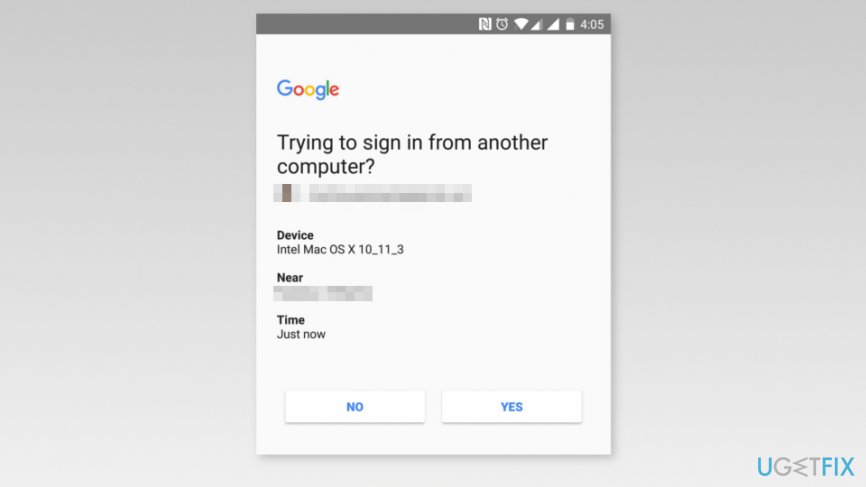
Note: If you do not see your phone listed, you have to click “Don’t see your device?” option and follow the guide here. You will need to confirm your phone number. - Soon as you click the button, you will receive a prompt on your mobile device. If the information on the prompt is correct, tap “Yes” button on the smartphone’s screen.

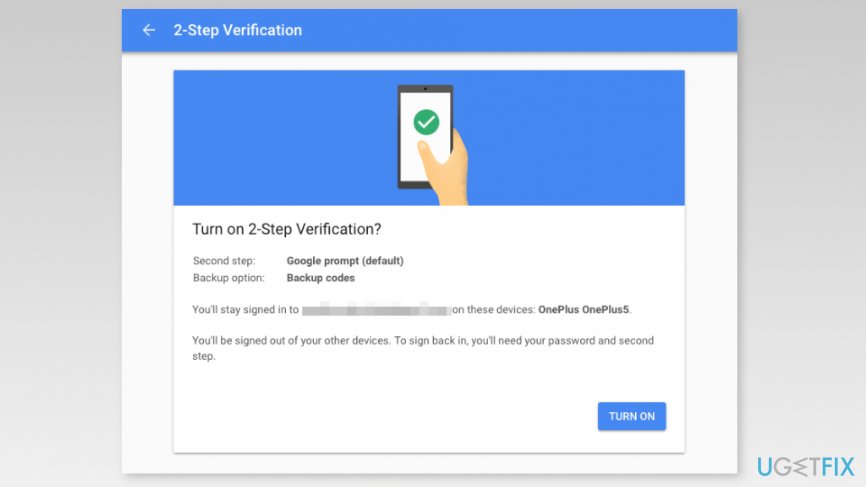
- Then you will see “Add a backup option” window where you have to choose alternative sign up method in case you lose your phone. You can set your phone number or click “Use Another Backup Option” which hides the list of backup codes which you have to print or download.
- Once you choose your alternative login solution, click “Next” button.
- Finally, you will have to click “Turn On” button to enable two-factor authentication on Google.

Turning off two-factor authentication on Google account
If for some reason you want to disable two-factor authentication on your Google account, you can do it simply. Follow these steps:
- Access your Google account.
- Navigate to “Sign in & security” section and choose 2-step verification.
- Sign in to your account by entering the username, password, and verification code if needed.
- Select “Turn off.”
- In the appeared pop-up confirm the action by clicking “Turn off” button.
Optimize your system and make it work more efficiently
Optimize your system now! If you don't want to inspect your computer manually and struggle with trying to find issues that are slowing it down, you can use optimization software listed below. All these solutions have been tested by ugetfix.com team to be sure that they help improve the system. To optimize your computer with only one click, select one of these tools:
Access geo-restricted video content with a VPN
Private Internet Access is a VPN that can prevent your Internet Service Provider, the government, and third-parties from tracking your online and allow you to stay completely anonymous. The software provides dedicated servers for torrenting and streaming, ensuring optimal performance and not slowing you down. You can also bypass geo-restrictions and view such services as Netflix, BBC, Disney+, and other popular streaming services without limitations, regardless of where you are.
Don’t pay ransomware authors – use alternative data recovery options
Malware attacks, particularly ransomware, are by far the biggest danger to your pictures, videos, work, or school files. Since cybercriminals use a robust encryption algorithm to lock data, it can no longer be used until a ransom in bitcoin is paid. Instead of paying hackers, you should first try to use alternative recovery methods that could help you to retrieve at least some portion of the lost data. Otherwise, you could also lose your money, along with the files. One of the best tools that could restore at least some of the encrypted files – Data Recovery Pro.
- ^ Margaret Rouse. Two-factor authentication (2FA). TechTarget. The network of technology-related websites and definition database.
- ^ Tina Sieber. What Is Two-Factor Authentication, And Why You Should Use It. MakeUseOf. The guide in modern tech.
- ^ Christina Chipurici. Hacked Email: Why Cyber Criminals Want to Get Into Your Inbox. Heimdal Security Blog. Cyber security advise.